Cloud technology has changed company operations by providing unattainable flexibility, scalability, and efficiency. The cloud has become essential to modern businesses, used for everything from daily operations to customer data storage. But there are significant drawbacks to these advantages. Insider attacks, ransomware, data breaches, and cloud misconfigurations expose companies to risks that are beyond the scope of traditional local security solutions.Due to their lack of complete visibility, cloud infrastructures are more vulnerable to security threats. A crucial line of defense against these problems is provided by Cloud Access Security Brokers (CASBs), which enable businesses to safely accept cloud usage while protecting their digital assets.
Table of Contents
What is A Cloud Access Security Brokers {CASB}?
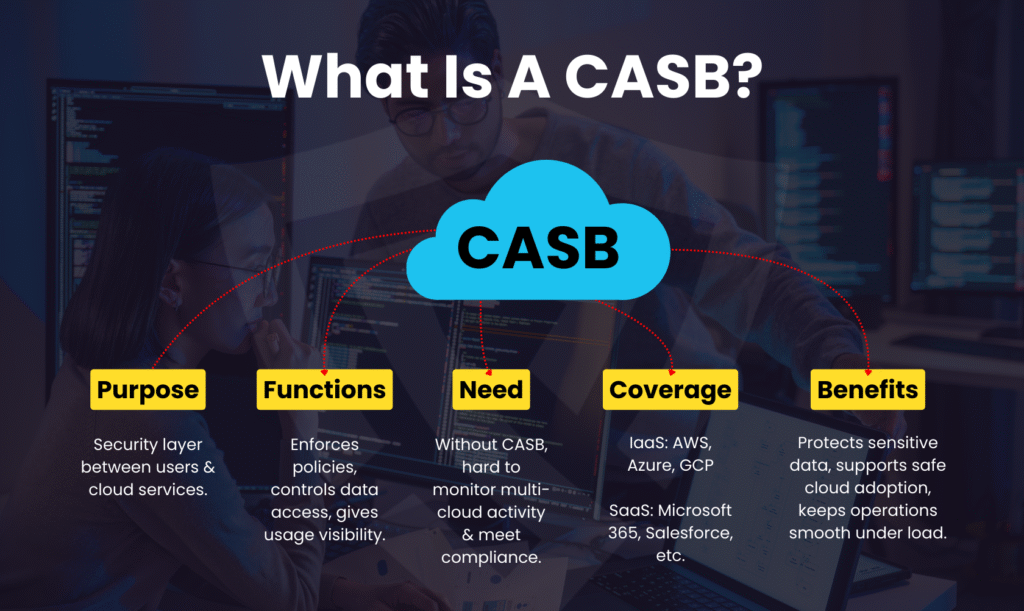
Cloud Access Security Brokers, or CASBs, are security solutions that monitor, manage, and safeguard cloud data access and usage by serving as a mediator between users and cloud services. It acts as a safeguard, enforcing security regulations, managing data access, and offering insight into the usage of cloud apps. Many firms find it difficult to keep an eye on activities across several cloud platforms without a CASB. CASBs provide the protection of sensitive data in IaaS platforms like AWS and Azure as well as SaaS apps like Salesforce and Microsoft 365. Their goal is straightforward but effective: to enable enterprises to use the cloud securely without delaying operations or lowering output in stressful circumstances.
Why are CASBs Important?
Cloud computing usage frequently increases more quickly than safety measures implemented by companies. Workers might utilize prohibited apps, keep private data in the wrong location, or access company data from risky devices. CASBs provide full visibility into cloud usage, helping in resolving these issues. They use techniques like tokenization and encryption to protect sensitive information, even in the unlikely case that it is misplaced or stolen. Real-time threat detection by CASBs includes malware, suspicious logins, and attempts at account hijacking. Additionally, by implementing uniform data protection standards across all platforms, they facilitate compliance with difficult industry regulations like HIPAA, GDPR, or PCI-DSS.
Benefits of CASBs for Business
CASBs are valuable because of the benefits they offer to businesses.CASBs provide enterprises with more visibility, more control, and safer methods to employ cloud services, among other advantages beyond information protection. CASBs are essential to establishing trust and security in the cloud, from stopping data leaks to guaranteeing regulatory compliance.
Stronger Data Protection : Tokenization and encryption are used by CASBs to protect sensitive data. Attackers cannot read data that has been lost or stolen. This helps companies in safeguarding financial data, client information, and intellectual property.
Reduced Risk : CASBs keep an eye on user behavior and identify dangers, including malware, unusual logins, and attempts at account hijacking. They reduce overall security risks and stop data breaches by identifying these early.
Better Control : Organizations can set clear regulations on who can access specific data, from what device, and under what circumstances by using CASBs. This guarantees that important information is only accessible to the appropriate individuals.
Regulatory Confidence : Businesses with strict regulations, such as healthcare, finance, or e-commerce, can depend on CASBs to automatically enforce compliance policy. They greatly simplify reporting, audits, and compliance with regulations like HIPAA, GDPR, and PCI-DSS.
The 4 Pillars of CASB
A CASB’s effectiveness is supported by four pillars. These pillars, which include visibility, compliance, data security, and threat prevention, serve as a framework for how businesses secure their cloud environments. Businesses can use CASBs to safeguard digital assets and keep control over cloud usage by being aware of these pillars.
Visibility : CASBs offer complete data on cloud usage throughout the company. They assist businesses in recognizing potential hazards and keeping control of their cloud environment by detecting shadow IT, tracking user activity, and identifying which applications are being used.
Compliance : CASBs assist companies in fulfilling legal obligations, including PCI-DSS, GDPR, and HIPAA. They simplify audits and guarantee that sensitive data is safeguarded while complying with industry and legal requirements by enforcing data-handling procedures, monitoring access, and producing reports.
Data security : CASBs safeguard private data sent or stored in the cloud. They use data loss prevention (DLP), tokenization, and encryption to make sure that private information is safe even if it is accessed by unauthorized parties or stolen in transmission.
Threat Protection : CASBs are able to identify and react to malware, suspicious logins, malicious behavior, and account hijacking. They offer real-time protection by keeping an eye on behavior patterns and integrating threat intelligence, preventing security events before they have a chance to cause damage to an organization.
How to Implement a CASB?
Depending on the devices, security objectives, and demands of an organization, there are various approaches to implementing Cloud Access Security Brokers (CASBs). Every deployment technique offers a balance between visibility, real-time protection, and usability. Businesses may select the best strategy for protecting their cloud environments by being aware of the difference between the three primary CASB deployment models— API-based scanning, forward proxy, and reverse proxy .
API Based Scanning
API-driven CASBs use their native APIs to connect directly with cloud platforms. They are great for auditing and compliance since they offer insight into user activities, saved data, and file sharing. They are simple to deploy and don’t interfere with workflows because they operate in the background. However, they lack real-time protection against upcoming dangers like malware downloads or unsafe user activity, and they primarily concentrate on data at rest.
Forward Proxy
A proxy is used by CASBs to filter user traffic before it enters the cloud service. This makes it possible to immediately implement security measures like preventing sensitive uploads or illegal logins. When traffic routing can be regulated on managed corporate devices, they work incredibly well. Despite providing strong real-time protection, their configuration is more complicated and might not be appropriate for personal or unmanaged devices that are not part of the company’s network.
Reverse Proxy
Traffic returning from the cloud service to the user is captured by reverse proxy CASBs, which are placed in front of the service. They are helpful for unmanaged devices like personal computers or mobile phones because they don’t require complicated network upgrades like forward proxies do. Without complete device control, they allow policy enforcement and safe access. However, not all cloud applications may be supported by reverse proxies, and there can sometimes be compatibility issues.
How CASBs Bridge the Security Gap?
Traditional security tools like antivirus software, firewalls, and secure web gateways are mostly made for on-premise networks. They are effective at keeping an eye on internal computers and devices, but they frequently fall short in protecting cloud-based resources, leaving companies exposed to online attacks. By immediately extending security controls to cloud apps, CASBs close this gap.
They keep an eye on user activity and access trends, identifying abnormalities such as big data transfers or logins from strange places. By enforcing similar security policies across SaaS, PaaS, and IaaS cloud platforms, CASBs guarantee that data protection, access control, and compliance are upheld consistently throughout the cloud ecosystem. By doing this, they establish a proactive, centralized layer of defense that lowers risk, stops breaches, and provides enterprises with complete insight into their cloud operations.
Key Functions of CASBs
Data Loss Prevention (DLP) : By monitoring file transfers, email exchanges, and cloud uploads, CASBs stop sensitive data from leaving the company. In order to maintain the security of financial data, intellectual property, and customer information while assisting with compliance with laws like GDPR and HIPAA, they enforce restrictions to prevent accidental or intentional data leaks.
Identity and Access Management (IAM) : To manage who has access to cloud resources, CASBs collaborate with (IAM) systems. In order to prevent insider threats and unauthorized access to important apps and data across several cloud platforms, they implement conditional policies, role-based access, and authentication to guarantee that only authorized users are allowed admission.
Tokenization and Encryption : CASBs safeguard private information by substituting tokens for it or transforming it into unreadable formats. It provides important data saved or transferred in the cloud an extra layer of security by guaranteeing that it is safe and unreadable by hackers even in the event that it gets hacked, lost, or stolen.
Threat Intelligence and Anomaly Detection : CASBs examine cloud activities to spot malware, unusual activity, and suspicious logins. They help firms react swiftly, reduce risks, and stop data breaches before they do serious harm by offering real-time warnings and insights into possible security problems.
Integration with other Security Solutions
SIEM Integration : CASBs are able to communicate with Security Information and Event Management (SIEM) systems by sending detailed logs, alerts, and user activity data. By centralizing monitoring and reporting, security teams can more effectively identify unusual activity, look into incidents, and address possible threats across all cloud apps.
Identity and Access Management (IAM) : To maintain user identities, regulate access permissions, and implement strong authentication techniques, CASBs interface with IAM technologies. This lowers the possibility of insider threats, guarantees that only authorized individuals have access to sensitive cloud resources, and offers a smooth method of integrating role-based policies across various cloud platforms.
Endpoint Protection : CASBs keep an eye on devices using cloud apps by integrating with endpoint security solutions. They can guarantee compliance to company regulations, enforce security procedures, and prohibit risky devices. This integration reduces the chance of malware or compromised devices causing data breaches in the cloud environment.
Layered Defense : To develop a multi-layered defense plan, CASBs collaborate with other security tools. Businesses can ensure complete protection across their whole cloud infrastructure by combining CASB capabilities with SIEM, IAM, and endpoint protection. This approach offers unified visibility, consistent policy enforcement, and real-time threat detection.
FAQ’s
What is a CASB’s primary objective?
By acting as a security gateway between users and cloud apps, a Cloud Access Security Broker (CASB) makes sure that all cloud activity is tracked and managed. Security policies are enforced, sensitive data is protected by encryption and tokenization, unusual or dangerous behavior is detected, and unauthorized access is prevented. CASBs assist companies in preserving regulatory compliance, lowering security risks, and securely utilizing cloud services without sacrificing productivity by offering insight into cloud usage and integrating with existing security solutions.
Why do modern businesses need CASBs?
CASBs are essential to enterprise security since cloud adoption is growing more quickly than traditional security solutions. They protect sensitive data, enforce security regulations, and keep an eye on cloud activity. Additionally, CASBs assist in ensuring regulatory compliance, stopping illegal access, and identifying dangers in real time. They lower risk and make it possible for businesses to use cloud services effectively and safely by giving them visibility and control across all cloud platforms.
Can SaaS and IaaS platforms be used with CASBs?
Yes, CASBs enable a variety of cloud services, including as IaaS platforms like AWS and Azure and SaaS apps like Microsoft 365 and Salesforce. Regardless of the service or provider, they guarantee consistent security and compliance by offering visibility, enforcing policies, and safeguarding data across all kinds of cloud environments.
Conclusion
These days, Cloud Access Security Brokers (CASBs) are an essential part of modern cloud security. Across cloud platforms, they offer visibility, data security, compliance assistance, and real-time threat detection. CASBs enable companies to properly use cloud technology while safeguarding sensitive data and upholding regulatory compliance by filling the gap left by traditional security measures. Effective CASB implementation guarantees that businesses may use the cloud effectively, safely, and with confidence.