Table of Contents
An Email Security Audit involves a systematic review of an organization’s email systems to find weaknesses, recognize possible threats, and verify adherence to security policies. It aids in revealing problems such as phishing threats, malware infiltration avenues, and attempts at unauthorized access. It bolsters overall communication safety by evaluating authentication protocols, encryption standards, and email configurations. Frequent audits reduce the likelihood of data breaches and protect confidential information from cybercriminals. This anticipatory strategy safeguards against developing cyber dangers while enhancing credibility and trust. In the current digital landscape, robust business operations rely on properly conducted email security audits.
Common Email Security Threats and Vulnerabilities
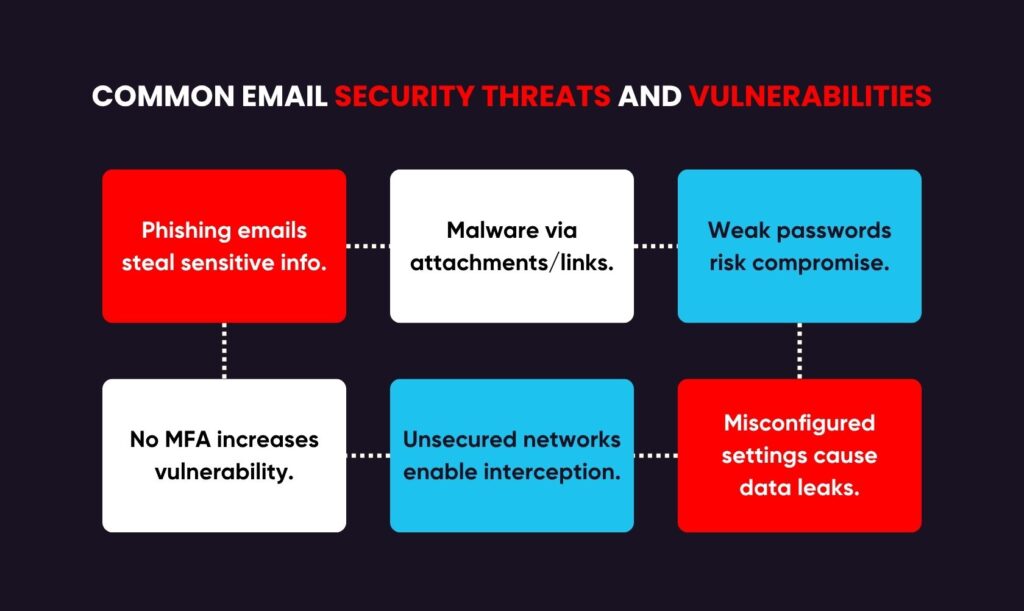
Email security threats and vulnerabilities include phishing attacks, where fraudulent emails deceive recipients into providing sensitive information, and malware that can compromise devices through harmful attachments or links. Weak passwords and the absence of multi-factor authentication increase the vulnerability of accounts to compromise. Unsecured networks may allow attackers to intercept emails. Incorrectly configured email settings may permit unauthorized access or data leaks. It is essential to remain cognizant of these risks in order to avert cyber incidents and protect information.
Key Steps Involved in Conducting an Email Security Audit
To conduct an email security audit means to verify that each component of the email system is secure and safeguarded. The initial step involves reviewing access controls and security policies. Then, look for dangers such as phishing links, malware, or dubious attachments. Next, verify the robustness of passwords, encryption methods, and spam filters. Detect and remedy any vulnerabilities or settings that are no longer current. Finally, compile a report detailing the findings and measures to enhance security moving forward. Regular audits guarantee continued protection and lower the likelihood of cyberattacks.
Best Practices for Securing Email accounts and servers

The effective methods for securing email accounts and servers involve employing strong, distinct passwords alongside multi-factor authentication to enhance security. Keeping software and security patches up to date on a regular basis helps seal vulnerabilities that attackers might take advantage of. By encrypting emails, you make sure that any sensitive data stays confidential while being sent. Setting up security settings and spam filters lowers the chances of phishing and harmful emails arriving in the inbox. Keeping an eye on account activity can swiftly reveal any suspicious conduct. By consistently adhering to these steps, a safer and more dependable communication environment is established.
By Integrating Multi-Factor Authentication (MFA) into E-mail Systems
By incorporating multi-factor authentication (MFA) into email systems, an additional security layer is provided that goes beyond merely using a password. It necessitates that users confirm their identity using an alternative method, like a code dispatched to a mobile device or an authentication application. This complicates the process for attackers to access accounts, even if they manage to obtain the password. To set up MFA, you must select appropriate authentication methods and activate them in the security settings of the email platform. Training users on effective use of MFA is crucial. To ensure ongoing protection against evolving threats, it is important to review and update MFA settings on a regular basis.
Visit PCI-DSS Compliance checklist Secure Your Payment Systems
Detecting and Preventing Phishing Attacks Through Audits
To detect and prevent phishing attacks through audits, it is essential to scrutinize email systems for any signs of unusual behavior and vulnerabilities. Through audits, one can find out about unusual login attempts, harmful links, and bogus emails. To prevent phishing attempts from reaching inboxes, security settings, spam filters, and authentication methods are evaluated. Training users to identify warning signs, such as unsolicited attachments or pressing requests, provides an additional safety measure. Detected threats are eliminated, and vulnerabilities in the system are promptly addressed. Regular audits facilitate the ability to stay ahead of phishing tactics and ensure secure communication.
Tools and Technologies for Effective Email Security Auditing

Effective email security auditing tools and technologies assist in recognizing risks and strengthen protection. This includes spam filters, malware scanners, and encryption tools to ensure the safety of messages. Audit software can monitor email traffic, identify unusual behavior, and produce comprehensive security reports. Tools for authentication such as DKIM, SPF, and DMARC assist in confirming senders and preventing fraudulent emails. Cloud-based security platforms provide real-time surveillance and threat identification. Employing a mix of these tools guarantees a more robust protection against cyber threats and maintains the reliability of email communication.
Maintaining Compliance with E-Mail Security Standard and Regulation
To ensure that email communication is safe and lawful, it is necessary to adhere to certain rules in order to comply with email security standards and regulations. This encompasses safeguarding sensitive information, employing encryption methods, and stopping unauthorized access. Frequent audits assist in confirming that all security measures comply with necessary guidelines such as GDPR, HIPAA, or other industry standards. To prevent legal problems, policies need to be revised in line with changing regulations. Everyone adheres to best practices due to training and awareness programs. Remaining compliant not only prevents penalties but also fosters trust in email communication.
Creating a Post-Audit Action Plan for Ongoing Email Security
By developing a post-audit action plan focused on ongoing email security, the results of an audit can be translated into tangible enhancements. This entails remedying recognized weaknesses, refreshing obsolete configurations, and boosting protective measures. To ensure that progress remains aligned with expectations, each task should be assigned a clear timeline. It is possible to check whether changes are having the desired effect through regular monitoring. It is important that the plan incorporates periodic evaluations to adjust to emerging threats. This method maintains the robustness of email systems and lowers the likelihood of future security problems.
Continue Reading Proton Mail Review: Is it the most secure Mail?
Conclusion
It is essential to conduct regular email security audits in order to protect sensitive data and guarantee compliance in the current environment of cyber threats. Organizations in Dehradun can bolster their defenses by implementing best practices such as multi-factor authentication, phishing prevention, and continuous monitoring. With the expert guidance of Senseacademy, Dehradun’s premier cybersecurity institute, and through a specialized course, individuals and businesses can secure their communications, foster trust, and remain resilient against emerging threats.
How does an email security audit strategically benefit an organization’s cybersecurity posture?
An email security audit provides a thorough evaluation of an organization’s email infrastructure, identifying systemic weaknesses, misconfigurations, and gaps in policy. In addition to threat detection, it bolsters the overall security framework by verifying authentication methods, encryption practices, and adherence to compliance.
How often should email security audits be performed to ensure operational integrity?
Although the best practice in the industry suggests audits every six months, the frequency should be determined by factors such as the organization’s risk appetite, regulatory context, and volatility of the threat landscape. To uphold security assurance, sectors or entities at high risk that handle regulated data—like finance, healthcare, or government—may need to implement audit cycles on a quarterly basis or even continuously, utilizing automated monitoring systems.
Which advanced tools and protocols are essential for conducting a high-fidelity email security audit?
A strong audit ecosystem comprises multiple defenses, such as heuristic spam filters, sandboxed malware analysis tools, and end-to-end encryption methods. To ensure that malicious activity can be identified and contained quickly, the core authentication protocols DKIM, SPF, and DMARC must be supplemented with anomaly detection systems, Security Information and Event Management (SIEM) integrations, and threat intelligence feeds.



