Operational technology (OT) forms the foundation of modern industrial operations, enabling real-time control, automation, monitoring, and managing physical systems, including infrastructure, machinery, and sensors in real time. It plays a crucial role across industries, like manufacturing, energy, utilities, and transportation. OT systems, such as SCADA, DCS, and PLCs, are responsible for managing vital functions that maintain uninterrupted industrial settings. As industries undergo digital transformation, the convergence of Information Technology and Operational Security is reshaping how organisations operate and secure their systems.
This article explores the fundamentals of OT, its key components, applications across industries and the growing need for strong OT security in a connected industrial ecosystem. From IT-OT convergence challenges to best security practices, it also provides a comprehensive overview to help professionals and organisations strengthen their operational resilience.
Table of Contents
Operational Technology
The term “operational technology” (OT) refers to the hardware and software systems used in industrial settings to monitor, regulate, and automate physical processes. It forms a basis for vital infrastructure, integrating digital technology with machines, sensors, and control systems to guarantee operational efficiency and real-time visibility. OT concentrates on managing and preserving the functionality, security, and dependability of physical systems, as opposed to traditional IT, which manages data and communications. OT is critical to the smooth, safe, and effective operation of critical infrastructure and industrial processes, from manufacturing facilities and electricity grids to oil and gas refineries, water utilities, and transportation networks.
ics-scada-security-testing-protecting-infrastructure-from-threats
How Operational Technology Works
Core Components of Operational Technology
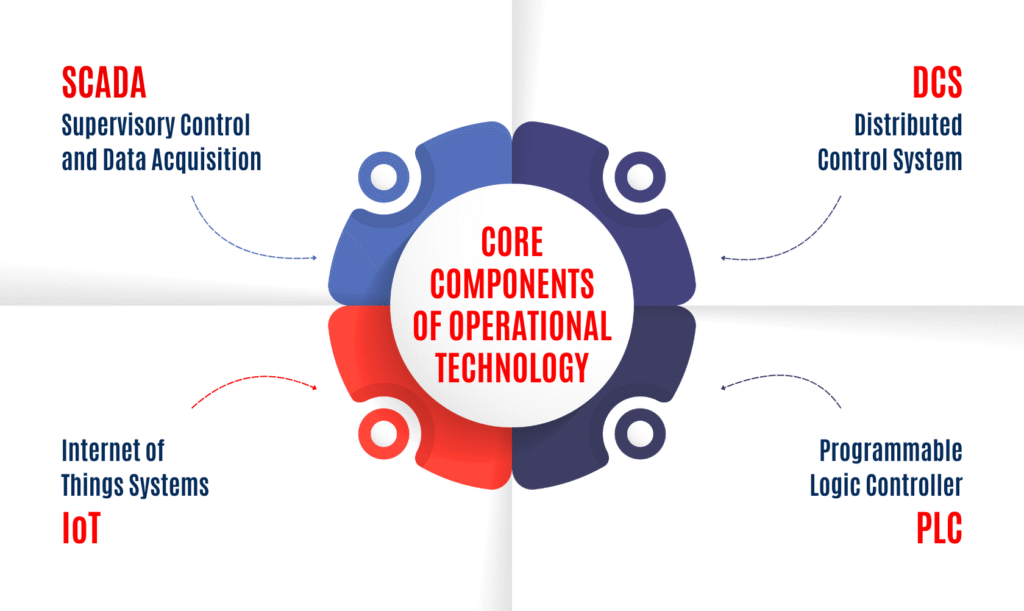
1 SCADA (Supervisory Control and Data Acquisition)
A centralized system called SCADA is used to monitor and control industrial processes across multiple locations. It collects data in real time from sensors and devices, displays it to operators on dashboards, and allows centralised control over infrastructure and machinery. SCADA is essential for large-scale systems that require constant monitoring and remote control, such as transportation networks, energy grids, and water treatment plants.
2. DCS (Distributed Control System)
DCS distributes control functions across multiple controllers rather than relying on a single centralized unit. DCS distributes control functions across several controllers. DCS distributes control functions across multiple controllers. It is commonly used in complex procedures that require exact control over temperature, pressure, and flow, such as the manufacturing of chemicals or the refining of oil. By distributing work, DCS improves dependability, minimises bottlenecks, and guarantees that operations may go without interruption even if part of the system fails.
3. Programmable Logic Controller, or PLC
PLCs are specialized industrial computers designed to automate specific tasks. They operate machinery like conveyor belts, motors, and pumps by executing preprogrammed logic. PLCs are essential for automation in the manufacturing, energy, and transportation industries because they are highly reliable, can survive challenging industrial conditions, and react quickly to changes in sensor input.
4. Internet of Things (IoT) Systems
IoT in OT offers real-time data exchange and analytics by connecting sensors, actuators, and devices to networks. Predictive maintenance, remote monitoring, and cloud platform integration for improved operational insights are all made possible by IoT devices. Because of this connectivity, OT systems can leverage AI, machine learning, and advanced analytics to enhance industrial operations’ productivity, safety, and decision-making.
Visit why-vapt-is-crucial-for-banks-financial-services
Interaction between Sensors, Actuators, Control and Systems
OT systems operate by receiving input from Sensors that track variables like temperature, pressure, or flow rate to provide information . Controllers, like PLCs and DCS, process this data before sending commands to actuators, which are machines that physically modify machinery, open valves, or regulate motors. In order to maintain optimal operational performance, this interaction creates a closed-loop system where measurements are continuously monitored and corrective measures are automatically implemented. By ensuring that physical systems react appropriately to changing circumstances, OT improves efficiency and safety.
Real-Time Monitoring and Automation
A crucial component of OT is real-time monitoring which allows operators to track system performance instantly and detect irregularities before they become more serious. Another crucial component is automation, which improves consistency and lowers human error by carrying out activities and control operations without human participation. OT systems, which serve as the basis for modern smart factories, energy grids, and industrial infrastructures, enable industrial facilities to run dependably, uphold safety standards, and maximize resource utilization by fusing continuous monitoring with automatic responses.
The Convergence of IT and Operational Security Challenges
Blurring Lines Between IT and OT
The line between information technology (IT) and operational technology (OT) is becoming more hazy due to the rapid pace of digital transformation. Traditionally, IT systems managed company data and communication, while OT systems worked in remote industrial settings, concentrating on managing physical operations. These days, technologies like cloud computing, networked devices, and the Industrial Internet of Things (IIoT) are bridging the gap between OT and IT to create integrated ecosystems where business and operational data interact.
Benefits of IT-OT Integration
- Enhanced Efficiency: Minimises the need for human intervention in industrial operations by automating workflows.
- Improved Data Visibility: promotes informed decision-making by offering real-time operational performance monitoring.
- Predictive maintenance
- using data from OT devices processed analyzed by IT systems, to maximizes resource use, and anticipates equipment breakdowns by IT systems.
- Operational Optimization– Supports better resource management, process enhancements, and general productivity.
- informed strategic planning- Industries can use operational data for long-term planning and performance improvement thanks to informed strategic planning.
Risks and Cybersecurity Challenges
- Increased Cyber Exposure- Enhanced Cyber Exposure: OT systems are more vulnerable to ransomware, malware, and targeted attacks when they are connected to IT networks and the internet.
- Legacy System Vulnerabilities: Because many OT devices and protocols were not built with modern cybersecurity features, they include vulnerabilities that can be exploited.
- Loss of Operational Continuity: Production, safety precautions, and vital services may be affected by cyber incidents in OT environments.
- Data Breach Risks– Integration increases unauthorized access to critical operational and commercial data.
- Complex Security Management: Advanced monitoring and unified cybersecurity techniques are necessary to provide uniform protection across IT and OT systems.
Continue Reading what-is-encryption-and-how-does-it-work
Common Operational Security Threats and Challenges
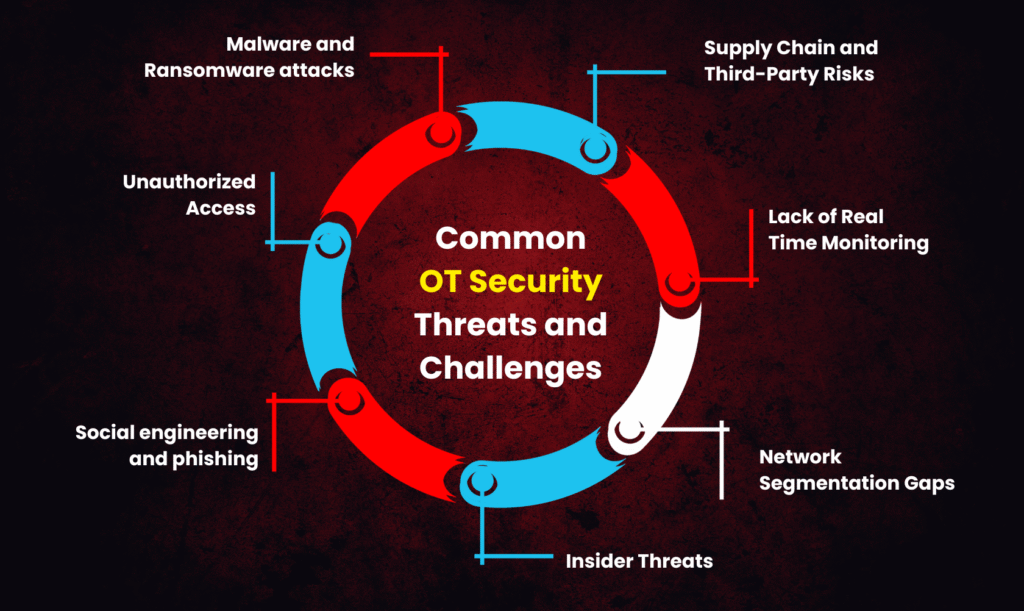
1. Malware and Ransomware attack
Ransomware and other malware that disrupts production processes are increasingly targeting OT systems. Critical control systems or data may be locked by such attacks until a ransom is paid.In industrial settings, this results in expensive downtime and possible safety risks.
2. Unauthorized Access
OT systems are frequently vulnerable to unwanted access due to weak authentication and shared user credentials.When an attacker gains control, they can change configurations, turn off systems, or steal private information. Both operational safety and system dependability are impacted by this.
3. Social engineering and phishing
Cybercriminals exploit human behaviour by tricking employees into downloading malware or revealing information about themselves. One of the most frequent ways to access OT and IT networks is still through phishing emails. A single error can lead to more significant industrial attacks.
4. Insider Threats
OT systems can be intentionally or unintentionally damaged by a person with authorized access. Vulnerabilities may be revealed or operations disrupted by carelessness, abuse, or malicious intent. Because of this, access controls and user behavior monitoring are crucial.
5. Network Segmentation Gaps
Lateral attacks are more likely when IT and OT networks are improperly segregated. Hackers can quickly enter crucial OT environments after breaking into an IT system. To contain possible invasions, segmentation must be done correctly.
6. Lack of Real Time Monitoring
OT settings are not continuously monitored in many firms. This makes it more difficult to find irregularities, intrusions, or illegal conduct. In order to prevent and address security breaches, timely visibility is essential.
7. Supply Chain and Third-Party Risks
Vulnerabilities may be introduced into OT networks by outside vendors or service providers. Entire systems may be compromised by malicious malware or unreliable maintenance equipment. Third parties must undergo thorough screening and security checks.
Why is Operational Security Important?
Operational technology (OT) security is essential for protecting the systems that manage crucial infrastructure, including manufacturing facilities, power plants, water treatment facilities, and transportation networks. Any disruption with these systems can cause widespread effects, ranging from public service failures to safety risks and production delays. A single cyberattack or system failure can result in operational failures, environmental harm, and even hazards to human safety because OT environments regulate physical processes that must run continually and safely.
Moreover, OT security ensures the availability, reliability, and integrity of industrial activities. Strong security procedures are crucial because the danger of cyber threats rises as digital transformation links OT with IT networks. Effective OT security helps businesses comply with legal requirements, preserve data accuracy, and foster confidence in their operational resilience in addition to averting monetary losses and downtime. Protecting OT systems is not only a technical necessity in today’s interconnected industrial ecosystem, but it is also a fundamental prerequisite for long-term sustainability, productivity, and safety.
FAQ’s
1. What is Operation Security?
Operational technology (OT) refers to Hardware and software systems used to monitor, regulate, and automate industrial processes. It includes systems SCADA, DCS, and PLCs that manage physical processes in industries like manufacturing, energy, utilities, and transportation.
2. Why is OT security important for businesses?
OT security is essential because it protects critical infrastructure against risks to safety, operational disruptions, and cyberattacks. Cybersecurity is crucial to industrial dependability and safety since a security breach in OT systems can stop production, harm equipment.
3. How is OT different from IT?
Operational technology (OT) works with regulating physical devices and processes, whereas information technology (IT) focuses on managing and processing digital data. While OT places a higher priority on system availability, safety, and real-time performance, IT guarantees data integrity and communication.
What are the main challenges in securing an OT system?
Securing OT systems is challenging due to legacy equipment, short update downtime, and greater with IT networks. Because of these variables, OT environments are vulnerable to malware, ransomware, and illegal access, requiring particular security measures and ongoing monitoring.
Conclusion
Critical industrial processes depend on operational technology (OT) to run safely, effectively, and continuously. Strong OT security is now more important than ever as industries adopt digital transformation and IT-OT integration. Beyond only protecting data, ensuring operational continuity, worker safety, and public confidence in vital services are all important aspects of protecting OT environments.
By adopting proactive security measures, infrastructure can survive changing cyberthreats by implementing proactive security measures, ongoing monitoring, and cooperation between IT and OT teams. Securing OT systems is a strategic concern for assuring sustainable and dependable industrial growth in an increasingly interconnected world, not just a technical objective.