What is a firewall?
How to perform firewall audit: A firewall is a significant part of network safety, acting as a cybernetic protector gate for inbound and outbound network traffic packages. When traffic does not see well-known safety necessities, the firewall swipes closed and blocks the network packages from developing. By observing and revising all the data entering or leaving a network, the firewall delivers improved security against illegal data contact but only if the firewall itself is fully efficient and in obedience with established guidelines.
A firewall audit is a multistep procedure that gives administrations vision into the position and efficiency of the firewalls connected through their network. These audits deliver reflectivity into possible weaknesses and the condition of networks going to and from firewalls. They also discover info about firewall variations since the last audit.
Firewalls are precarious components within a greater network safety construction, helping as gatekeepers for inbound, outbound, and inside network traffic. As traffic streams through the network, firewalls sited at each network segment calculate traffic packets, blocking traffic that does not meet pre-established safety limits. While firewalls are operative network safety tools, they must be kept up-to-date and regularly observed. That’s where the firewall audit procedure comes in.
Why firewall audit important?
To comprehend the significance of a firewall audit, it’s essential to first comprehend how a firewall works. Firewalls are accomplished by autograph-design appreciation to analyze and associate packets beside an expansive database of known attack vectors, malicious code, or threats, limited contact for traffic that matches any of these hazards.
But these offerings assured problems that may be abused. For one, firewalls must be continually efficient to take into account quickly developing malicious payloads and threats. At the same time, incorrectly-arranged guidelines can announce flaw in firewalls that may be abused to increase illegal contact. In both circumstances, the incapability of the firewall to detect, separate, and limit malicious packets may place the whole network in significant danger. At the same time, handling firewalls can be very difficult, mainly within multifaceted systems. Lack of reflectivity and imperfect certification stands in the method of actual firewall organization, possibly revealing sensitive systems and information to threats
The firewall audit as a conception is constructed on the knowledge that safety is more than just utensils; it’s an on-going procedure in which present defenses are continually revised, audited, and enhanced upon to deliver the best-likely network and data safety. Frequently and reliably accomplished, firewall audits are a vital element in confirming firewall capability, and play a key part in refining network safety, companywide.
Firewall Audit Benefits
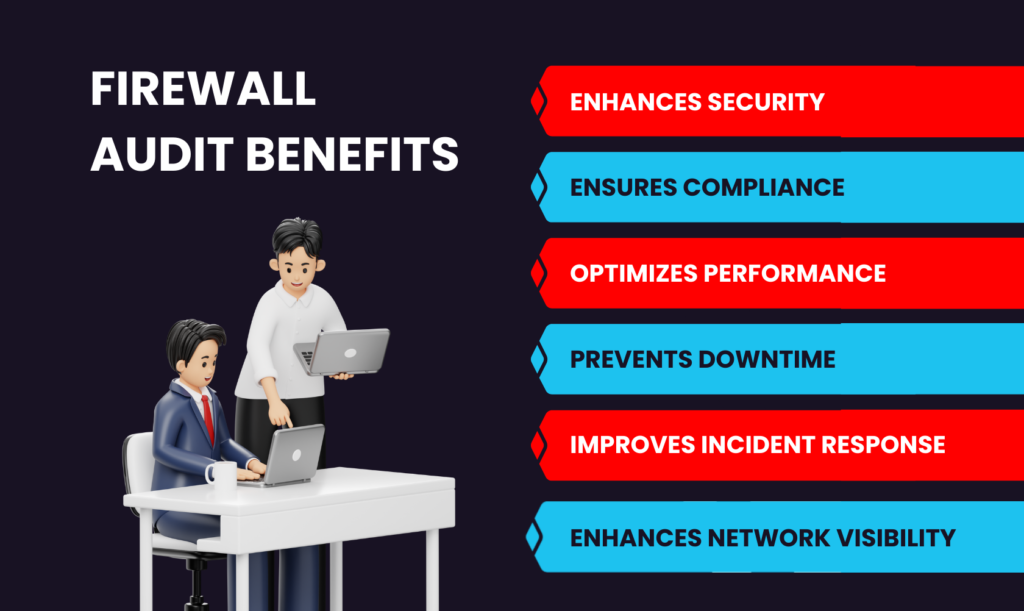
| Benefit | Description |
| Enhances Security | Identifies misconfigurations that could lead to unauthorized access. |
| Ensures Compliance | Meets regulatory standards such as PCI-DSS, HIPAA, and ISO 27001. |
| Optimizes Performance | Removes redundant and outdated firewall rules. |
| Prevents Downtime | Detects and mitigates potential risks before they cause system failures. |
| Improves Incident Response | Helps detect and respond to security threats more efficiently. |
| Enhances Network Visibility | Provides insights into traffic patterns and anomalies. |
How Does a Firewall Audit Work?
A firewall audit is a detailed process that required your IT and safety crews to look carefully at your firewall certification and variation organization procedures. Audits increase queries about firewall functionality, as well as power crews to get granular about who’s in charge of firewall guidelines. They lay a foundation for nonstop network safety updates and developments.
To effectively perform an audit, first decide your audit’s goals and gather the information your team wants. Then, analysis your firewall guidelines and whether they’re still a good fit for your safety organization and complete network safety. Your crews should also know who’s blameable for the request and maintenance of each rule. A good firewall review must end with an evidently planned review in the upcoming, as well as analysis procedures so you know if the firewall really works.
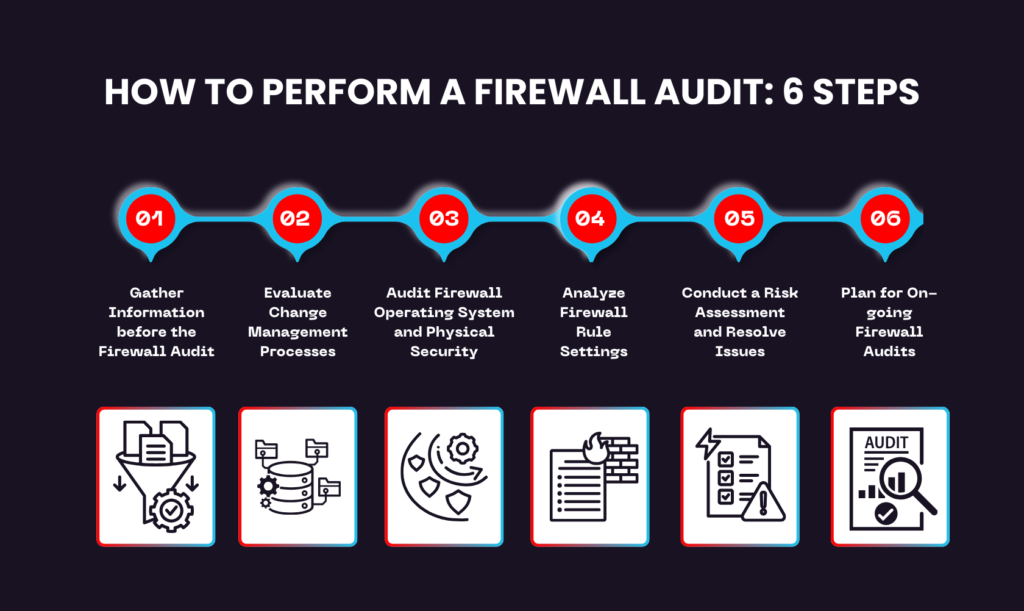
How to Perform a Firewall Audit: 6 Steps
Gather Information before the Firewall Audit
Before initiating a firewall audit, ensure you have comprehensive visibility into your network infrastructure, including hardware, software, security policies, and user interactions. Gather and centralize critical data to create a single source of truth for the audit. Key information includes:
| Task | Description |
| Review previous audit reports | Examine past findings and applied firewall rules. |
| List all ISPs and VPNs | Identify every network connection utilized by the organization. |
| Collect security policies | Ensure documented and undocumented policies are available. |
| Retrieve firewall logs | Access logs to analyze traffic patterns and security events. |
| Vendor and configuration details | Record OS versions, default settings, and patches. |
Evaluate Change Management Processes
A firewall audit is an opportunity to assess the organization’s approach to managing firewall changes. Establishing a clear and consistent change management process prevents security lapses and ensures uniform implementation. Key considerations include:
| Task | Description |
| Identify responsible personnel | Define roles for managing firewall changes. |
| Review approval workflows | Ensure proper authorization procedures are in place. |
| Verify testing documentation | Confirm firewall changes undergo testing before deployment. |
| Standardize change tracking | Implement a structured approach for logging and monitoring modifications. |
Audit Firewall Operating System and Physical Security
A robust security strategy includes both software and physical security measures. An effective firewall should be capable of detecting and mitigating cyber threats swiftly. Key assessment areas include:
| Task | Description |
| Restrict physical access | Limit access to firewall servers to authorized personnel. |
| Evaluate OS security hardening | Ensure configurations align with security benchmarks. |
| Assess device administration policies | Verify access control and authentication settings. |
| Apply vendor patches | Keep firewall software up to date with the latest security updates. |
Analyze Firewall Rule Settings
Optimizing firewall rules helps improve efficiency, eliminate unnecessary rules, and enhance security. Key areas to focus on include:
| Task | Description |
| Identify redundant rules | Remove outdated or conflicting firewall rules. |
| Prioritize security and performance | Ensure effective rule ordering. |
| Verify object configurations | Ensure objects follow proper naming conventions. |
| Assess VPN settings | Remove expired or unused VPN users and groups. |
| Evaluate permissive rules | Adjust or remove overly permissive policies. |
Conduct a Risk Assessment and Resolve Issues
Performing a risk assessment ensures that firewall configurations align with security policies and industry regulations. Areas to evaluate include:
| Task | Description |
| Assess firewall policies | Determine whether firewall rules comply with internal security policies. |
| Identify risky services | Review access permissions for critical areas like the DMZ and external networks. |
| Detect high-risk rules | Identify firewall rules that allow overly broad access. |
| Check compliance with standards | Align configurations with regulatory frameworks such as PCI-DSS, ISO 27001, and NERC CIP. |
Plan for On-going Firewall Audits
Maintaining a strong firewall security posture requires on-going audits and continuous improvements. Implementing a structured, repeatable audit process ensures long-term security and compliance. Key considerations include:
| Task | Description |
| Document audit processes | Establish a detailed and repeatable audit methodology. |
| Leverage automation | Reduce errors by incorporating automated auditing tools. |
| Communicate policy changes | Ensure all modifications to firewall rules are recorded and shared with relevant stakeholders. |
| Schedule periodic reviews | Establish a regular audit cycle for continuous monitoring and improvement. |
Best Practices for Firewall Audits
- Perform audits quarterly or annually to maintain security.
- Use automated auditing tools like FireMon or AlgoSec for efficiency.
- Keep backup copies of configurations before making changes.
- Train IT staff on firewall best practices and security trends.
- Document all findings and create an action plan for improvements.
Optimizing Firewall Management with ServiceNow
Firewalls act as the first line of defense, blocking unauthorized access attempts by cybercriminals. However, as cyber threats grow more advanced, businesses must implement stronger oversight and control measures. Conducting regular firewall audits is crucial for maintaining a robust security posture, but true protection requires a more comprehensive approach. This is where ServiceNow provides an effective solution.
ServiceNow Firewall Audit and Reporting addresses common visibility and compliance challenges that hinder effective firewall management. By leveraging ServiceNow Discovery, organizations gain complete insight into their firewall infrastructure and related processes, ensuring regulatory compliance while minimizing security risks. IT teams and authorized users can centrally manage firewall policies, utilizing dashboards and business insights for a seamless, integrated approach.
Additionally, users and firewall owners can submit and track requests through ServiceNow portals, streamlining communication and issue resolution. Automated workflows further enhance efficiency by reducing manual workloads for IT teams and eliminating operational bottlenecks. With ServiceNow Firewall Audit and Reporting, businesses gain full firewall visibility, integrated data management, and improved compliance. Protect the systems that safeguard your business with a smarter, more transparent firewall management solution.
Top 3 Firewall Audit Providers
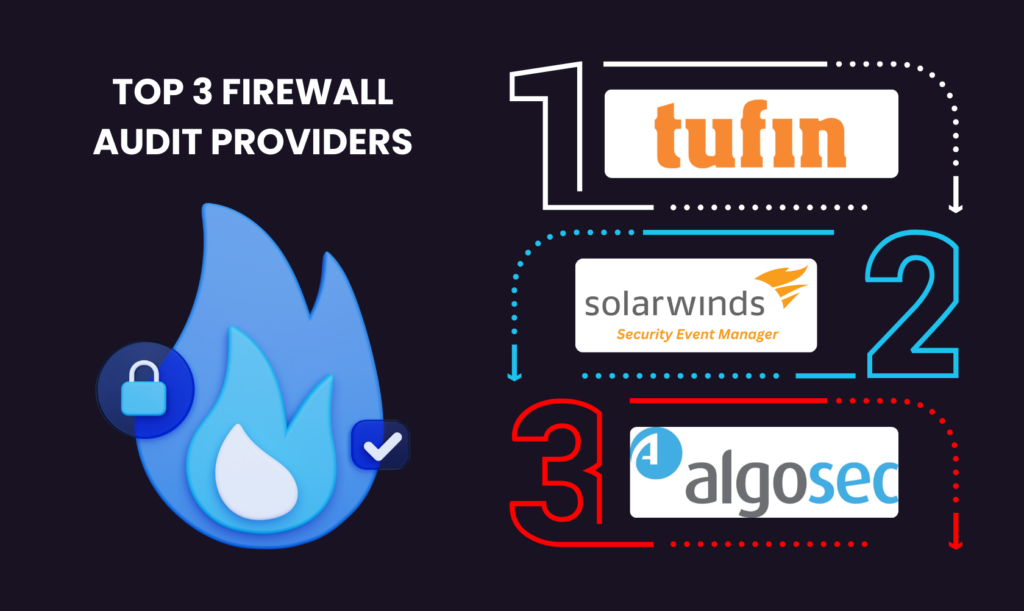
If you’re searching for a reliable firewall auditing solution, Tufin, SolarWinds SEM, and AlgoSec are among the leading options in the cybersecurity market. These tools offer essential features such as compliance auditing, firewall rule analysis, and network scanning to help organizations maintain security and regulatory compliance.
Tufin
Tufin is designed to assist businesses in achieving and maintaining compliance with regulations such as HIPAA, PCI-DSS, and GDPR. It automates audit report generation and alerts security teams when firewall configurations fail to meet predefined security policies. Tufin offers three subscription plans—SecureTrack+, SecureChange+, and Enterprise—with pricing available upon request from its sales team.
SolarWinds SEM
SolarWinds Security Event Manager (SEM) is an all-in-one cybersecurity management tool that enables businesses to centralize log data, generate audit reports, and receive real-time security alerts. It helps IT teams monitor network activity effectively. SolarWinds SEM offers subscription licenses starting at $2,992 and perpetual licenses beginning at $6,168. For customized pricing tailored to your business needs, contacting their sales team is recommended.
AlgoSec
AlgoSec specializes in firewall auditing and compliance management, ensuring that firewall rule changes align with industry standards like PCI, SOX, and HIPAA. It also documents the approval process for rule modifications to maintain transparency. Businesses can obtain a customized pricing plan by requesting a quote through AlgoSec’s sales team or one of its authorized partners.
These top firewall audit providers help organizations strengthen their security, compliance, and risk management while ensuring optimal firewall performance.
Explore More: How to perform wireless Penetration Test
FAQ
How often should a firewall audit be conducted?
Firewall audits should be performed at least once a year, though more frequent reviews (quarterly or semi-annually) are recommended for high-security environments.
What are the most common firewall misconfigurations?
Common misconfigurations include overly permissive rules, outdated firewall policies, missing updates, and unmonitored access control lists.
Can firewall audits be automated?
Yes, many tools like FireMon, AlgoSec, and Tufin automate firewall audits by analyzing rule efficiency, identifying risks, and ensuring compliance.
How can I ensure compliance with firewall regulations?
Ensure firewall settings align with industry standards such as PCI-DSS, HIPAA, ISO 27001, and NERC CIP. Regular audits and documentation is a key to maintaining compliance.
What should be included in a firewall audit report?
A comprehensive report should detail firewall configurations, detected vulnerabilities, rule efficiency, access control settings, compliance adherence, and recommended improvements.



