Table of Contents
Google confirmed that in June, skilled hackers gained access to one of its corporate Salesforce installations, stealing contact details belonging to small and medium-sized enterprises.
The event shows how social engineering techniques are becoming increasingly complex and successful while also highlighting the growing threat of voice phishing attempts directed at enterprise cloud settings. Data privacy, cloud security, and third-party integrations have all become major issues as a result of this failure. This hack offers cybersecurity pros and students a practical case study to comprehend the vulnerabilities that might arise even in systems operated by multinational tech giants.
How Data Breach was detected?
The first indication of the vulnerability came from unusual activity in Google’s integrated Salesforce environment. Security analysts raised internal alarms by identifying improper access patterns and suspicious API calls. After looking into it, it was found that hackers had taken advantage of a weakness to obtain sensitive data. Google’s Threat Intelligence Group (GTIG) claims that UNC6040, a financially driven threat cluster that specializes in voice phishing attacks aimed at hacking Salesforce instances for extensive data theft, was responsible for the attack. Later the incident was handled quickly by Google’s security team.
How Hackers Tricked employees to access company data
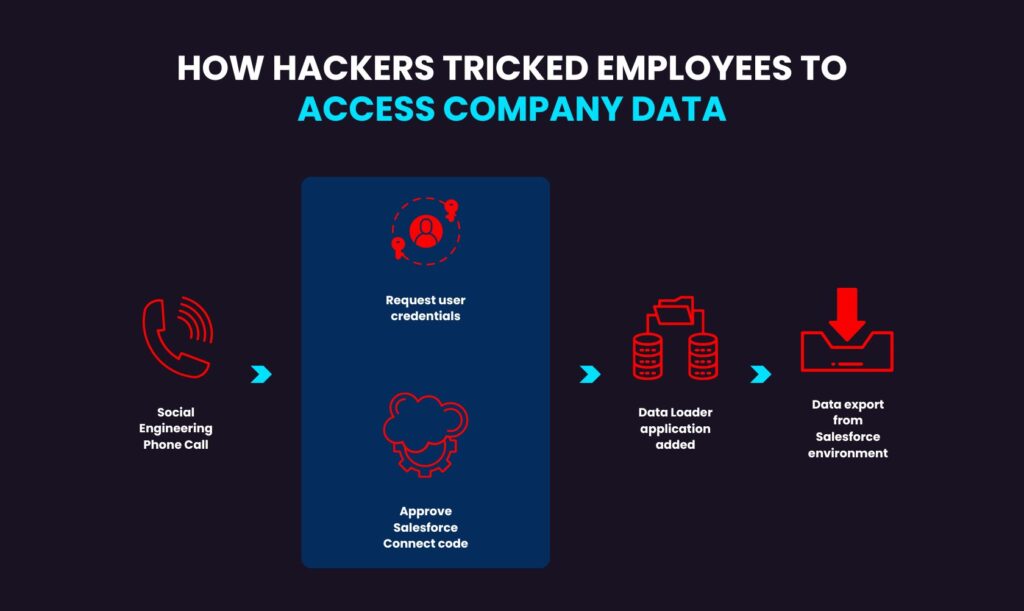
According to the company’s analysis, attackers were able to successfully retrieve data within a limited window before access was blocked. Only basic business information, such as company names and contact details that are generally accessible to the public, was exfiltrated. In order to deceive victims, UNC6040 uses highly convincing telephone-based social engineering techniques, with operators posing as IT support staff. Threat actors usually target workers in multinational companies’ English-speaking subsidiaries, deceiving them into taking steps that allow them to access Salesforce environments without authorization. Tricking victims into allowing malicious linked apps to access their company’s Salesforce interface is a crucial part of their strategy.
Potential Impact on users and Businesses
Users may be at risk of identity theft, phishing scams, and data loss as a result of the breach, leaving them open to other cybercrimes. Businesses are concerned about data privacy, customer confidence, and regulatory compliance as a result of the incident, particularly those that depend on Google or Salesforce services. Financial losses and operational interruptions could ensue, particularly if sensitive client data is at stake. This emphasizes the practical repercussions of inadequate third-party security measures for cybersecurity professionals and students. In contemporary commercial settings, it also emphasizes the necessity of enhanced data governance, incident response plans, and frequent audits.
How Google and Salesforce responded post breach

After discovering the attack, Google quickly alerted its incident response team and it worked with Salesforce to isolate the affected systems. To stop additional data loss, suspicious access tokens were terminated and emergency patches were applied. Both businesses started informing authorities and impacted users after starting a thorough forensic investigation. Google improved monitoring and third-party integration evaluations, while Salesforce strengthened its API security procedures. Their prompt, open response reduced the harm and rebuilt confidence.
Visit Secure Your Online Storefront Adv-E-Commerce
What Cybersecurity Professionals and students can learn from this breach?
For professionals and students studying cybersecurity, the Google-Salesforce hack provides important practical insights. It shows how improperly secured third-party integrations could compromise even the most advanced systems. The significance of putting Zero Trust models into practice where no system or user is automatically trusted. Or students, this is an opportunity to learn about the detection, reporting, and mitigation of breaches. It serves as a reminder to experts to maintain current knowledge of emerging dangers, conduct routine system audits, and implement stringent access restrictions. It highlights that cybersecurity is a continuous, intentional activity rather than a one-time setup.
Preventive measures: how you can secure your systems
Using multi-factor authentication, creating strong passwords, and limiting user access according to responsibilities are the first steps in system security. Continuously patch and update software, particularly third-party programs like Salesforce. Use real-time monitoring, firewalls, and endpoint security to identify attacks early. Never assume that a connection is secure; instead, adopt a Zero Trust strategy. For professionals and students alike, continuous training, security audits, and keeping up with emerging risks are essential. Maintaining cybersecurity requires constant effort.
Also Read Secure Source Code Review-Why it’s Non-Negotiable
The Importance of Third-Party Risk Management
Even the most secure systems may have hidden vulnerabilities due to third-party platforms like Salesforce. A single weak link can expose the entire network when sensitive data is accessible to integrated systems. Limiting access permissions, keeping an eye on third-party activities, and evaluating vendor security procedures are all part of managing this risk. To guarantee compliance, organizations must set up strict security agreements and carry out frequent audits. Neglecting third-party risks can result in serious data breaches, monetary losses, and harm to one’s reputation. An effective third-party risk management plan is crucial in the linked digital world of today.
Role of Automation in Threat Detection and Response
Automation is essential for detecting and addressing cyberthreats more quickly than human procedures could. AI and machine learning enable systems to recognize odd trends, highlight abnormalities, and even respond quickly to neutralize threats. As a result, response times are shortened, damage is reduced, and security teams can concentrate on making intricate decisions. Regular scans, round-the-clock network activity monitoring, and real-time threat intelligence updates are all possible with automated technologies. Automation is not only useful in today’s rapidly changing threat landscape, but it is also necessary to keep one step ahead of attackers.
Also read https://techcrunch.com/2025/08/06/google-says-hackers-stole-its-customers-data-in-a-breach-of-its-salesforce-database/
Why are hackers increasingly targeting third-party interfaces like Salesforce?
Although not all third-party tools are as secure as others, they frequently have extensive access to private systems and data. Because they can get around basic system defenses if a connected platform is weak, attackers target these integrations as weak points.
What should be done right away if a breach affecting third-party sites is discovered?
In addition to notifying users and initiating a forensic investigation, organizations ought to disconnect the impacted integration and invalidate any suspicious access tokens. To stop more harm, it’s also essential to coordinate patching and breach security with the third-party provider.
In what ways this hack be a teaching moment for bettering cybersecurity procedures?
It emphasizes the necessity of ongoing observation, proactive risk assessments, and robust vendor management procedures. It also emphasizes the significance of planning with tried-and-true incident response strategies and assuming breach scenarios.




2 thoughts on “New Google’s Data Breach Hackers Exploit Salesforce”