Table of Contents
Data breaches are becoming increasingly common and impacting sectors such as banking, IT, finance, and healthcare. There is no organization that is 100% safe, the average cost of a breach for critical infrastructure companies was $4.82 million. Companies use Vulnerability Assessment and Penetration Testing (VAPT Testing), a thorough security testing methodology that finds and fixes flaws before attackers take advantage of them, to combat these cyberthreats. We will go into much more detail about VAPT in this blog, including its approach, significance, and business benefits.
What is VAPT ? and Why do you need it ?
The organized cybersecurity procedure known as Vulnerability Assessment and Penetration Testing (VAPT) is intended to identify, evaluate, and fix vulnerabilities in networks, applications, and systems. It blends two important strategies: The goal of vulnerability assessment, or VA, is to find a system’s security flaws. Penetration Testing (PT): Evaluate how vulnerable those vulnerabilities are by simulating actual attacks. Businesses benefit from VAPT: Fixing vulnerabilities before hackers can take advantage of them will help prevent data breaches. Fulfill the requirements for compliance: Security testing is required by laws such as GDPR, PCI-DSS. Preserve brand reputation: Financial and reputational harm might result from a data breach.
Also read Best VAPT tools
Difference between vulnerability assessment and Penetration Testing
Finding security flaws in systems, networks, or applications without exploiting them is known as vulnerability assessment, or VA. Providing an in-depth review of all possible risks, ranking vulnerabilities according to their seriousness, and outlining corrective actions to address them are its main objectives. In order to ensure ongoing security monitoring and timely detection of emerging threats, VA is typically carried out on a frequent basis.
By simulating actual attacks, penetration testing (PT) goes beyond detection to exploit vulnerabilities found and evaluate their true impact. It offers a more thorough and useful understanding of how an attacker may compromise the system, frequently supplying proof-of-concept exploits. PT is typically carried out to verify defenses and test incident response capabilities on a regular basis or following major system changes.
VAPT Methodology, Step-by-Step process
An organized methodology is used in the VAPT (Vulnerability Assessment and Penetration Testing) process: Pre-assessment is the first step in defining the scope and goals, and information gathering is the next step in gathering system data. Penetration testing then simulates actual attacks, and analysis evaluates the outcomes. The findings are then presented in Reporting, and the issues found are resolved in Remediation. Ongoing enhancements are guided by consulting and support, and the system’s increased security is lastly confirmed by certification.
Know more about VAPT
Types of VAPT, Which approach fits your needs
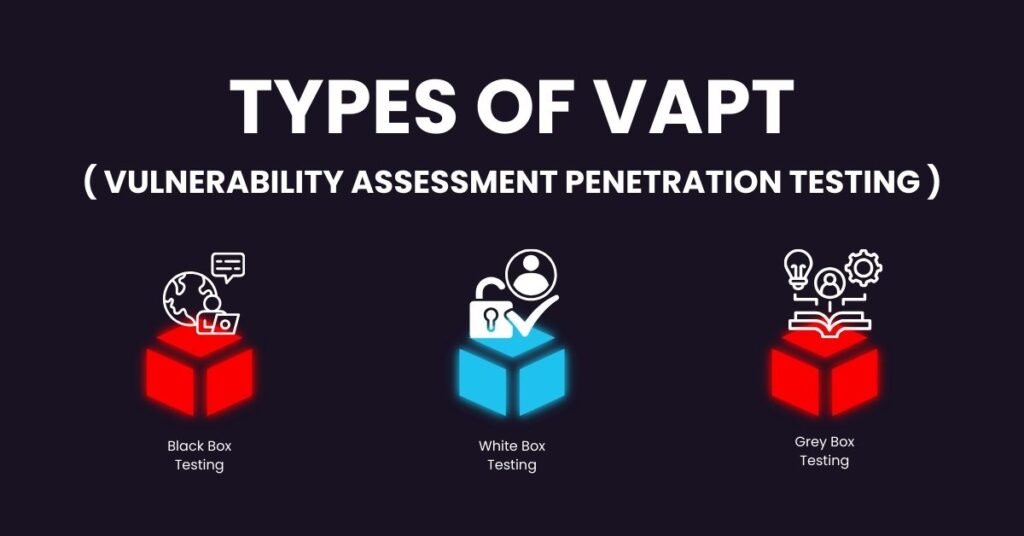
There are three primary methods for doing VAPT: Grey Box, White Box, and Black Box testing. Black box testing simulates the viewpoint of an external attacker by having testers have no prior knowledge of the system. White box testing enables a thorough security analysis by providing testers with complete access to internal data. Grey box testing provides a realistic and balanced evaluation by combining both with a limited understanding of the technology. Your objectives will determine the best strategy; select Black Box for simulating real-world attacks, White Box for carefully reviewing code and architecture, and Grey Box for a combination of efficiency.
Common Tools used in VAPT

Common VAPT tools help in locating, evaluating, and taking advantage of security flaws. Nessus is frequently used for vulnerability detection and compliance checks. Ethical hackers can mimic actual cyberattacks with Metasploit. For web app testing, Burp Suite is crucial since it may identify problems like SQL injection. OpenVAS provides vulnerability scanning for networks and systems in an open-source manner. Wireshark, Nmap, and Acunetix help with traffic analysis, mapping, and scanning. Nikto looks for configuration errors and out-of-date software on web servers.
Benefits of VAPT
Beyond only identifying security vulnerabilities, VAPT improves total cyber defense. In addition to building a solid portfolio of real-world testing experience and supporting acknowledged certifications that certify expertise, it improves practical, hands-on skills in finding and correcting vulnerabilities. In addition to providing firms a competitive edge through proactive threat detection and strong security measures, VAPT promotes career growth by expanding compliance expertise for standards like ISO 27001 and PCI DSS.
Conclusion
In the quickly changing digital world of today, VAPT has emerged as a crucial procedure for protecting networks, apps, and systems from online attacks. VAPT provides an organized way to strengthen security defenses, from comprehending its philosophy and different testing methodologies to becoming proficient with key tools and staying ahead of market trends. By spotting vulnerabilities before attackers can take advantage of them, it not only safeguards important data but also promotes compliance, increases organizational resilience, and builds trust.
Why is VAPT significant, and what is it?
A combined security technique called VAPT (Vulnerability Assessment and Penetration Testing) is used to find, examine, and take advantage of security flaws in networks, applications, or systems. It’s crucial because it enables businesses to identify vulnerabilities before hackers take advantage of them, strengthening data security and compliance.
What are the VAPT process’s primary steps?
Planning, scanning, vulnerability analysis, exploitation, and reporting are all common steps in the VAPT process. Every stage guarantees that vulnerabilities are carefully found, examined, and recorded, along with practical remedy suggestions.
Which VAPT tools are frequently used?
Popular VAPT technologies include OpenVAS for open-source vulnerability management, Metasploit for penetration testing, Nessus for vulnerability detection, and Burp Suite for web application testing. Accurate and effective security evaluations are made possible by these tools.



