Every business in the modern digital world depends significantly on technology to manage client data, conduct everyday operations, and provide services. No system is ever totally protected from cyberattacks, even with advancements in security technologies and testing techniques. Even well-protected systems may have undiscovered vulnerabilities in software, websites, or applications that are missed by traditional security checks. Hackers are always coming up with new ways to take advantage of vulnerabilities. Programs like bug bounty come into play here. They boost overall security testing by serving as an extra layer of protection that enables ethical hackers to look for weaknesses before criminals can take advantage of them.
Table of Contents
What is a Bug Bounty Program?

Organizations can formally ask ethical hackers, sometimes referred to as security researchers, to examine their systems and apps for vulnerabilities by implementing a bug bounty program. Businesses encourage trusted hackers to identify and report vulnerabilities rather than waiting for attackers to take advantage of them. These researchers are compensated with benefits, which can be cash or recognition. As an expansion of traditional security testing, bug bounty programs bring in a wider range of experts. Organizations can find hidden dangers that automated systems or internal teams might overlook by taking this proactive approach.
Why Bug Bounty matters in security testing?
Vulnerability scans, code reviews, and penetration tests are frequently included in security testing. These are important but they might not identify every problem. Through the use of independent security researchers who adopt an attacker’s mindset, bug bounty schemes provide an extra layer of protection.
Real World testing
Security testing usually includes penetration tests, code reviews, and vulnerability scans. While these are important, they may not catch every issue. Bug bounty programs add another layer of protection by bringing in independent security researchers who think like attackersThe mindset of bug bounty hunters is similar to that of malicious hackers, which makes their testing realistic and more comparable to real world attack scenarios. Researchers use their imagination, expertise, and special methods to find hidden defects, in comparison with automated technologies that follow to set rules. This helps in finding vulnerabilities that traditional scans or code reviews might miss. Bug bounty testing helps companies better understand how attackers might compromise their systems by mimicking real attack techniques.
Continuous Security
Traditional penetration tests are frequently planned for once or twice a year, with significant intervals between. On the other hand, bug bounty programs never stop, providing corporations with continuous protection. This implies that security researchers are already searching for flaws whenever new features, fixes, or updates are released. The possibility that vulnerabilities may go undiscovered for extended periods of time is decreased by continuous testing. It creates an atmosphere in which risks are promptly identified, allowing companies to address them before cybercriminals take advantage of them.
Cost – Effective
It might be expensive to hire a full-time security team or conduct regular penetration tests, particularly for small and mid-sized enterprises. By just paying for results, bug bounty programs lower this expense. It is a flexible and scalable option because organizations only pay researchers when they discover real risks. Rather than allocating a set budget for planned tests, businesses can more effectively distribute their security expenses. Every dollar spent will immediately increase system security due to our pay-for-results concept.
Broader coverage
Researchers from all around the world, each with their own specialties, resources, and methods, come together through bug bounty programs. Because of this diversity, systems may be checked from a variety of perspectives, which makes it more difficult for vulnerabilities to go undetected. While some researchers may focus on web apps, others might be more interested in cloud or mobile security. A tiny internal security staff was unable to carry out this broad coverage on their own. Organizations may strengthen and increase the dependability of their security by utilizing talent from around the world.
How a Bug Bounty Program Works
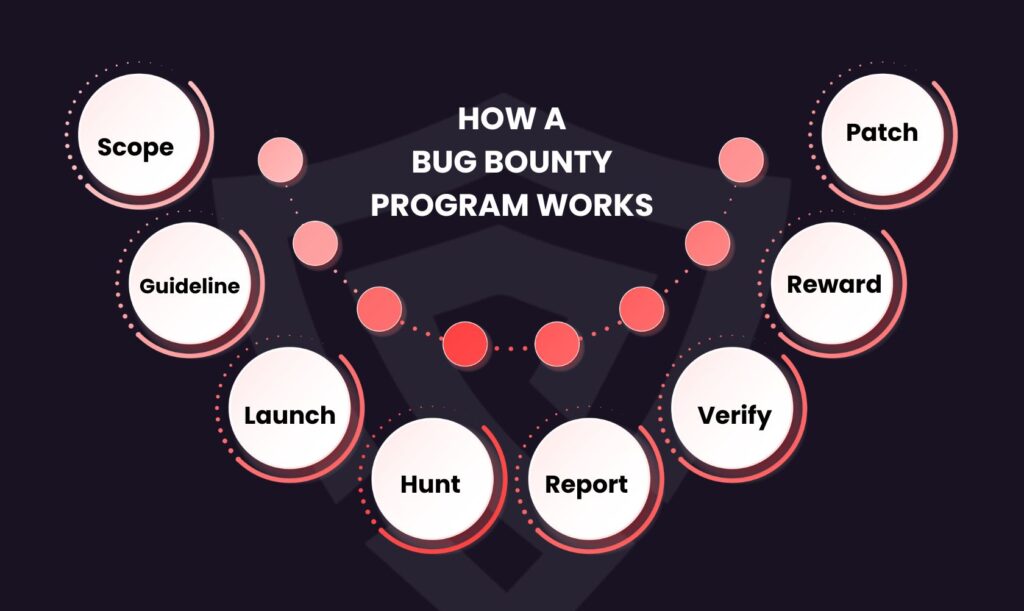
Determining which systems or apps can be tested is part of the first stage in establishing the scope of a bug bounty program. Clear guidelines are then established so that researchers are aware of which techniques are permitted and which areas are prohibited. After the program goes live, ethical hackers look for flaws and provide thorough reports. After reviewing each report, the organization verifies the problem and, if the findings are authentic, awards the researcher. This work as an organized strategy that ensures a structured approach in which security flows are found appropriately, reported securely, and fixed before attackers may take use of them.
Bug Bounty vs. Traditional Security Testing
Penetration Testing
Structured and time-bound, penetration testing is a task performed by an expert security team. It commonly focuses on important systems and applications and follows a planned scope and timetable. By generating cyberattacks in a controlled setting, these tests help organizations in identifying vulnerabilities before actual attackers do. Despite offering an entire view of the security position at the time, penetration testing could miss newly discovered vulnerabilities later on. For this reason, in order to remain safe, businesses frequently repeat them on a regular basis.
Bug Bounty Programs
Using a bug bounty program is similar to inviting trustworthy hackers—also known as security researchers—to examine your systems for vulnerabilities. These initiatives remain open and invite participation from specialists worldwide, rather than being restricted to a single team or brief assignment. Every researcher uses unique techniques to help in identifying various kinds of hidden faults. New problems can be reported at any moment because the application runs continuously. This strategy is inexpensive and very successful since businesses reward useful findings. The two approaches work well together. Traditional testing provides a solid base, but bug bounty programs provide an additional layer of protection by identifying potential vulnerabilities.
Types of Bug Bounty Programs
Bug bounty programs are usually divided into three types. Public programs are available to everyone worldwide, which frequently attracts a lot of researchers. Private programs is allowed to only invited members of a select group of reliable specialists. Time-bound challenges are designed to quickly identify problems by running for a short time, usually during events or the launch of new software. Every kind has benefits. Time-bound programs are helpful for quick testing, private programs guarantee quality, and public programs permit wide coverage. Businesses frequently select the kind according to their risk tolerance and security requirements.
Challenges in Bunty Bounty Programs
Although bug bounty systems work well, there are drawbacks. Reviewing the large number of duplicate or poor-quality reports that organizations may receive might take a lot of effort. Gaining the trust of researchers also requires making sure that incentives are fair and payments are fulfilled on time. Another difficulty is striking a balance between security and transparency; companies need to give researchers enough details to do efficient testing without disclosing private company information. Enterprises sometimes use specialized platforms to handle bug bounty programs effectively in order to get around these problems, which simplifies the process for both enterprises and researchers.
Advantages for businesses
Having a bug bounty program has several advantages. It shows a strong dedication to security, which fosters stakeholder and customer trust. By identifying and fixing problems before hackers do, it lowers the chance of expensive data breaches. Additionally, bug bounty programs give firms access to a global network of experts, providing them with a variety of skills and new insights. This crowdsourcing method frequently finds weaknesses that inside teams might overlook. Furthermore, it promotes an active culture of constant development in which security is viewed as a continuous duty rather than a one-time event.
Future of Bug Bounty Programs
The complexity of digital systems is increasing the demand for bug bounty programs. The attack surface is growing as cloud computing, mobile applications, and Internet of Things (IoT) devices become more common. It might not be possible to keep up with traditional security testing alone. It is expected that bug bounty programs will become more effective in the future as they further integrate automation and artificial intelligence. Businesses that implement these initiatives today will be able to ward off advanced cyberattacks. A proactive approach to stronger cybersecurity protection is represented by bug bounty programs.
FAQ’s
Is it safe for businesses to operate bug bounty programs?
Yes, bug bounty programs are secure as long as they are properly run. To prevent fraud, businesses establish boundaries, specify what systems can be tested, and provide clear guidelines. The organization and researchers are both protected by legal restrictions. Businesses make sure reports are handled securely and ethically by utilizing reliable systems. These programs, when properly designed, enable safe testing, build defenses, and shield company activities from damage.
Which sectors gain the most from bug bounty programs?
Bug bounty programs are especially beneficial to industries that manage sensitive data. Because they contain important data like financial records, medical information, and personal information, the finance, healthcare, e-commerce, government, and technology sectors are frequently the targets of cyberattacks. Bug bounty programs assist these sectors in identifying and addressing vulnerabilities before criminals take advantage of them. Organizations may strengthen their protection and increase their trust with stakeholders and customers by hiring qualified researchers from around the world.
Which tools are frequently used by bug bounty hunters?
To find vulnerabilities, bug bounty hunters use a combination of advanced instruments and specially written programs.Popular options include Wireshark for traffic analysis, Nmap for network scanning, and Burp Suite and OWASP ZAP for web app testing. Additionally, they use automation tools to expedite scanning and Google Dorks for customized searches. When paired with imagination and expertise, these tools aid in identifying flaws that traditional methods could overlook.
Conclusion
In today’s security testing, bug bounty programs are essential. Organizations can more quickly and efficiently identify vulnerabilities by combining the advantages of conventional techniques with the novel insights of international security researchers. In addition to shielding systems from any intrusions, these initiatives show a dedication to upholding strict security guidelines. In the current cybersecurity environment, bug bounty programs are an essential tool since, despite certain hurdles, the advantages justify the drawbacks. Their position will only become more significant as technology advances, contributing to the creation of a more secure and safe online environment for all users.




One thought on “Role of Bug Bounty in Cyber Defense”