Many of the messages that arrive in phones and inboxes every day have the purpose of tricking consumers into making quick mistakes. Some appear as urgent security alerts, some duplicate well-known internet services, and some even look like bank updates.Phishing is the strategy used behind these messages. Although these messages might appear harmless at first, they frequently contain hidden risks. It gets harder to tell the difference between real and fake as cybercriminals have become smarter at disguising their traps. Because of this, it’s more important than ever to recognize these scams fast in order to be secure online.
Table of Contents
What is Phishing?
Phishing is a kind of cyberattack in which hackers pretend to be trustworthy businesses or people in an attempt to trick victims into revealing personal information. These attackers often use phone calls, texts, or emails that appear authentic but are fake. Phishing primarily aims to obtain credit card numbers, usernames, passwords, and other private information. Anyone who uses internet services, such as social media or bank accounts, might be the victim of phishing schemes. Because human error is a major factor in phishing, attackers use psychological tricks like rewards, fear, or hurry to get people to react without thinking.
How Phishing Works?
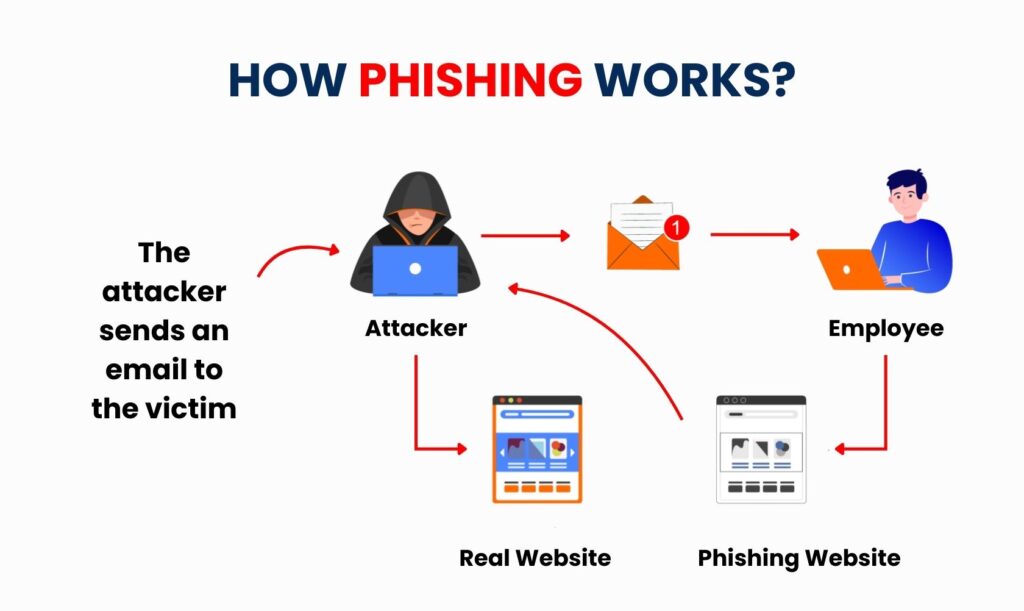
Phishing attacks mostly use social engineering, a technique in which hackers take advantage of human nature rather than directly entering systems. Typically, a phishing attempt starts with an urgent-seeming message, such as an email warning that your account will be blocked if you don’t take immediate action. Frequently, this letter includes a fake attachment or link that takes the person who received it to a fake website. The website can look just like the real one, tricking users into entering their login information. Attackers can use or sell the accounts or personal data they obtain after this information is entered.
Types of Phishing
Cybercriminals use a variety of techniques to trick people, and phishing can take many different forms:
Email Phishing: The most popular kind is email phishing, in which fake messages are sent to look as though they are from trustworthy companies. In order to convince recipients to click on links or download documents, these emails frequently contain urgent messages or alarming statements. A fake website designed to obtain login information or infect the device with malware may be accessed by clicking on the link.
Spear phishing: It is a highly focused attack that targets particular people or businesses. In order to make the email seem authentic, attackers frequently collect personal information like names, job titles, or corporate information. These messages are more difficult to notice since they are highly tailored and appear relevant to the recipient’s work or personal life.
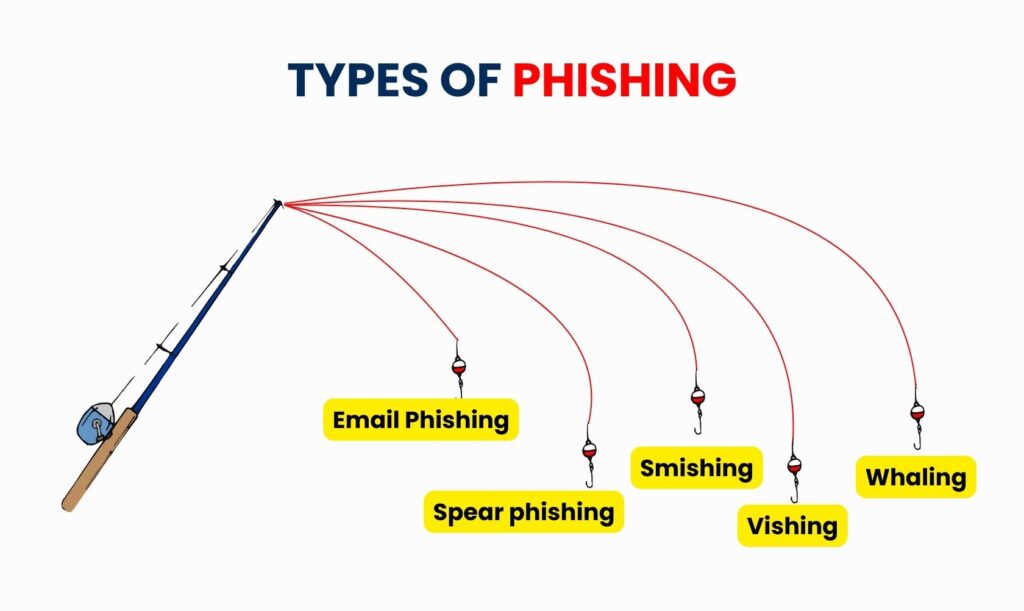
Smishing: In this Phishing is done via SMS messages” Attackers can appear as delivery services, banks, or other reliable organizations while sending messages. By requesting sensitive information or including harmful links, the messages trick users into reacting right away without checking the source.
Vishing: it is a type of phone phishing in which the attacker pretends to be a representative of a government agency, bank, or tech support. They build a sense of urgency and use convincing language to obtain private data, including passwords, PINs, and account numbers. Because the call appears to be professional, victims might not suspect anything.
Whaling: A very advanced type of phishing that targets decision-makers or senior executives is called “whaling.” The mails frequently include urgent business requests, legal alerts, or papers with an official look. Executives may unintentionally disclose confidential company information because these emails seem genuine and important.
Phishing Websites and Malicious Links
Phishing websites are expertly constructed fakes of trustworthy websites that mimic well-known services like email providers, online banking, and shopping portals. Attackers design these websites to look like the authentic ones as closely as possible, using language, layouts, and logos to trick users. Attackers quickly obtain personal information, financial information, and passwords when someone enters them. Phishing emails, SMS messages, and social media posts frequently connect to these fake websites. Malicious links can potentially download malware automatically onto a device, giving attackers further access to control systems or private information.
Phishing attacks also frequently use malicious URLs. Although they might look like regular URLs in messages, they frequently lead visitors to dangerous websites or cause malware downloads. To make links look authentic, attackers use strategies like URL shortening and misspelled domain names. Emails, texts, online messages, and even pop-ups on websites might include these links. Users unintentionally corrupt their devices or provide hackers access to private data by clicking on the link. It is important to use precaution and double-check links before clicking in order to prevent these risks.
How To Recognize Phishing Scams?

Phishing schemes can be easily identified by looking for common warning indicators. Keep a look out for emails or messages that create a sense of urgency, such limited-time deals or threats of account closure. Spelling errors, odd syntax, or suspicious sender addresses that don’t correspond to the actual company are common in phishing mails. Phishing emails may contain links that appear to be genuine but actually lead to fake websites. When an email requests private information, such as banking details or passwords, that is another warning sign. Avoiding these traps can be achieved by remaining alert and thoroughly examining before clicking or responding.
Consequences of Phishing Attack
Phishing attacks can have adverse effects on people and businesses. A single error, such as disclosing your password or clicking on a malicious link, might have serious consequences.
Identity Theft: Attackers may pose as victims by using stolen personal data, such as government identification documents, usernames, and passwords. The victim may experience long-term issues as a result of fraudulent purchases, illegal accounts, or misuse of personal data.
Financial Loss: Payment or banking information is frequently the goal of phishing. Attackers may steal credit card information, drain accounts, or conduct illegal activities, which could lead to disputes with banks or service providers as well as immediate financial loss.
Data Breach in Companies: Phishing can reveal confidential company information to groups. This includes trade secrets, internal communications, and consumer information, all of which may result in fines and legal problems.
Loss of Customer Trust: Clients and customers may become less confident in the business’s ability to protect their information if phishing results in compromised data. Long-term business connections and reputation may suffer as a result.
Malware and Network Infections: Phishing assaults can infect devices with spyware, ransomware, or malware. These viruses have the ability to propagate throughout networks, interfering with business processes, stealing more data, or bringing down systems.
How to Avoid Phishing?
Verify the sender: Pay close attention to the phone number or email address. Phishing communications frequently come from addresses that look like real ones, sometimes with only a single letter changed or a new domain used. Verifying the sender twice helps you avoid falling for fake messages that seem real.
Avoid clicking suspicious links: Before clicking,over any link to discover its actual destination. Phishing links may take you to fraudulent websites that install malware or steal your login information. It is safer to visit the official website immediately if a message appears strange or unexpected.
Avoid downloading unexpected attachments: Files from unreliable sources might be infected with malware, ransomware, or viruses. Download attachments only from contacts you have confirmed, and ask the sender for clarification before opening.
Type website addresses by hand: Enter the website address into your browser by hand rather than through links in messages. This ensures you visit the correct site and prevents fraudulent pages that mimic authentic websites.
Use strong, unique passwords: Avoid using the same password across several accounts. Strong, one-of-a-kind passwords lower the possibility of account takeover in the event that a phishing attack steals credentials.
Enable multi-factor authentication (MFA): It makes it far more difficult for hackers to access accounts even if they know your password. MFA adds a second verification step, like a code or app notification.
Keep software updated: Update your browsers, operating system, and security applications on a regular basis. Security fixes that stop malware, phishing attempts, and other online dangers are frequently included in updates.
Training Employees to Recognize Phishing
Employees are frequently the first line of defense against phishing in firms. Staff members can spot fake emails, suspicious links, and other warning signs with the use of training programs. Frequent awareness training sessions guarantee that staff members are aware of the signs of phishing and how to react to them. Simulated phishing tests are another tool that businesses may employ to get their teams ready for actual attacks. By establishing a “human firewall,” companies lessen the likelihood that workers may share private information or click on harmful links. Strong awareness and training not only safeguard business data but also foster a secure work environment.
Real world examples of Phishing Attacks
Example 1: The Phishing Attack on Google Docs (2017)
A popular phishing scam in 2017 used a fake Google Docs invitation to target Gmail users. The receiver was asked to open a document in an email that seemed to be from a person they knew. Attackers gained access to the user’s Google account and contacts when they clicked on the link. Because it automatically delivered the identical fake invitation to every contact on the victim’s list, the attack spread quickly. This incident, which affected millions of people and highlighted the significance of checking links before clicking, demonstrated how phishing can take advantage of trust and social connections.
Example 2: Ubiquiti Networks’ Business Email Compromise (BEC) (2015)
Employees at Ubiquiti Networks were instructed to move money to foreign accounts in 2015 by emails claiming to be from business officials. The attackers were successful in stealing $46.7 million from the emails, which were essentially phishing attempts. With a focus on financial gain, this example demonstrates how phishing can use social engineering to target enterprises. It also illustrates the danger of email-based fraud in business settings, highlighting the importance of strict financial protocols and verification in avoiding such losses.
Technologies & Tools to Prevent Phishing
Since phishing attempts are always changing, it is important to have several levels of prevention in place. A combination of technological tools and security procedures are used by modern businesses and people to stop hackers from stealing confidential data. Here is a look at some of the best anti-phishing tools on the market right now.
Email security gateways: As the initial line of defense, email security gateways are essential. They look for spoofing indicators, malware attachments, and suspicious URLs in receiving messages. Cutting-edge systems can automatically quarantine dangerous emails and utilize machine learning to identify new phishing tactics. These gateways reduce the probability that users will click on dangerous links by preventing phishing at the inbox level.
DNS Filtering Tools: DNS filtering keeps users from visiting websites that are known to be dangerous or fraudulent. The DNS filter compares the domain to threat intelligence databases when a link is clicked. Users are warned or sent to a safe page if they are flagged. In order to prevent a website from becoming extensively destructive, DNS filters frequently keep an eye on recently registered domains, which are commonly used by attackers for phishing attempts.
Multi-Factor Authentication (MFA) : By requiring a second form of verification, such as a temporary code, authentication app, or biometric check, multi-factor authentication (MFA) improves account security. MFA stops unwanted access even in the case that a phishing attempt is successful in stealing a password. MFA lowers the possibility of breaches brought on by compromised credentials by requiring it for internal systems, cloud services, and email accounts..
Browser Security Extensions: By identifying doubtful domains, malware downloads, and hazardous websites, browser extensions serve as a real-time firewall. Before users submit critical information, they frequently show visual safety indicators and prevent access to phishing websites. These extensions, which are seamlessly integrated into regular web browsing, offer a useful extra layer of security for online banking, email checking, and shopping.
Anti-Malware and Endpoint Protection Software: These programs check computers for spyware or malware that has been installed through phishing links or attachments. To find suspicious activities, they offer behavioral analysis and real-time monitoring. By safeguarding individual devices, these technologies help stop malware from propagating throughout corporate networks, preventing phishing attempts from developing into more serious security issues.
Training and Simulation Tools for Phishing: The weakest link in security is frequently human error. Organizations can test staff members with realistic simulated emails and monitor their responses by using phishing simulation tools. By raising awareness and reinforcing safe practices, this practical training enhances technical defenses and lowers the likelihood of successful attacks.
Threat Intelligence Platforms: These platforms collect information regarding questionable domains, active phishing campaigns, and attacker activity. This information can be used by organizations to proactively block emerging threats, update blacklists, and identify penetration trends early on. IT teams can react swiftly and remain ahead of new phishing techniques thanks to ongoing monitoring.
Secure Email Authentication Protocols (SPF, DKIM, DMARC): Email authentication protocols help verify the legitimacy of incoming messages. SPF ensures the sending server is authorized for the domain, DKIM adds a cryptographic signature, and DMARC enforces rules for handling unauthenticated messages. Together, these protocols prevent spoofed or fraudulent emails from reaching users, adding a strong foundation for email security.
Email authentication systems that help confirm the authenticity of incoming messages include Secure Email Authentication systems (SPF, DKIM, and DMARC). DKIM adds a digital signature, DMARC enforces guidelines for managing unauthenticated messages, and SPF makes sure the sending server is approved for the domain. When combined, these techniques provide a solid basis for email security by preventing consumers from receiving spoof or fraudulent emails.
Why Awareness is Key to Preventing Phishing?
The best defense against phishing is still human awareness, even with the importance of technology and tools. Attackers frequently use trickery to get victims to make quick choices without giving them much thought. Phishing efforts can be prevented by remaining alert, challenging suspicious communications, and double-checking information before replying. Campaigns for awareness and ongoing education maintain security information current and new. People and organizations may stay clear of phishing traps by exercising caution and awareness. Ultimately, the greatest strategy to lower risks and maintain online safety is to be alert.
FAQ’s
What if I unintentionally disclose private information?
Take quick action if you discover that you have given a suspicious source your financial or personal information. First, create strong, one-of-a-kind passwords for all accounts that could be impacted. Even if someone knows your password, you can still add an additional layer of security by turning on multi-factor authentication (MFA). Keep a careful eye on your accounts for any odd activity, like unauthorized transactions, strange emails, or login attempts. As soon as you can, let your bank, credit card company, or IT department know so they can take precautions. Lastly, to minimize possible damage and stop such attacks, think about informing the appropriate authorities or cybersecurity platforms about the occurrence.
Is phishing becoming more common?
Yes, phishing has increased significantly in quality and frequency in recent years. Attackers now have more ways to target people and organizations due to the growth of internet services, remote work, and digital communication. Advanced tactics like social media frauds, targeted spear phishing, and fake websites that nearly seem like real ones are all used in modern phishing campaigns. Cybercriminals also use holidays, current affairs, and popular subjects to make messages appear urgent or relevant. Relying solely on technical tools is insufficient due to the rapid evolution of phishing tactics; awareness, verification, and careful online conduct are necessary for staying safe.
Is it possible for social media to host phishing attacks?
Phishing attacks are prevalent on social media sites, actually. Attackers may pose as trustworthy connections and send fake friend requests, messages, or links. These messages frequently direct you to harmful downloads or fake login pages that steal your financial or personal data.
Conclusion
Phishing is still one of the most common and harmful internet hazards that affects both consumers and businesses. Despite the strong protection offered by technologies like email gateways, DNS filtering, multi-factor authentication, and anti-malware solutions, hackers continue to take advantage of human weaknesses. To lower risk, it’s critical to recognize warning indications, exercise caution when clicking links or opening attachments, and double-check communications before acting. Equally important are awareness and continual education, which build a human firewall to support technical defenses. Everyone may reduce their exposure to phishing and maintain safer online relationships by combining alertness, wise online practices, and the appropriate tools.