We live in the modern digital age where businesses depend significantly on networks to function effectively and hold sensitive data. They are also at risk of online hazards like malware, phishing, and hacking because of their dependence on it. Corporate network monitoring and protection require a Security Operations Center (SOC). However, it might be costly and complicated to develop a fully functional SOC internally. SOC-as-a-Service (SOCaaS) is useful in this situation. Without requiring an internal SOC team, SOCaaS provides expert-driven, cloud-based security monitoring and incident response. It helps businesses save time and money while staying protected..
Table of Contents
Who needs SOCaaS?
Organizations that want strong cybersecurity but lack the resources or know-how to establish an internal SOC can benefit from SOCaaS. SOCaaS allows all of these enterprises to maintain strong security while lowering operational complexity, for example:
Small and Medium Businesses (SMBs): Even though these businesses usually have small IT expenses, they are still at risk for phishing, spyware, and ransomware. Advanced protection and monitoring are offered by SOCaaS without the expense of a full-time in-house security staff.
Large Enterprises: Due to their numerous offices, servers, and cloud services, big businesses require ongoing oversight. They can effectively maintain security across all sites with the help of SOCaaS. Finance and healthcare: These sectors are governed by strict regulations and handle private client information. SOCaaS protects important data while guaranteeing compliance.
Remote Workforces: Businesses that have workers that operate from different places are prone to cyberattacks. To safeguard the company, SOCaaS remotely monitors networks and devices.
Startups: Although they can’t afford full-time security personnel, startups need strong safety measures from the beginning. As businesses scale, SOCaaS provides them with expert protection.
Which Cyber Threats are Monitored by SOCaaS?
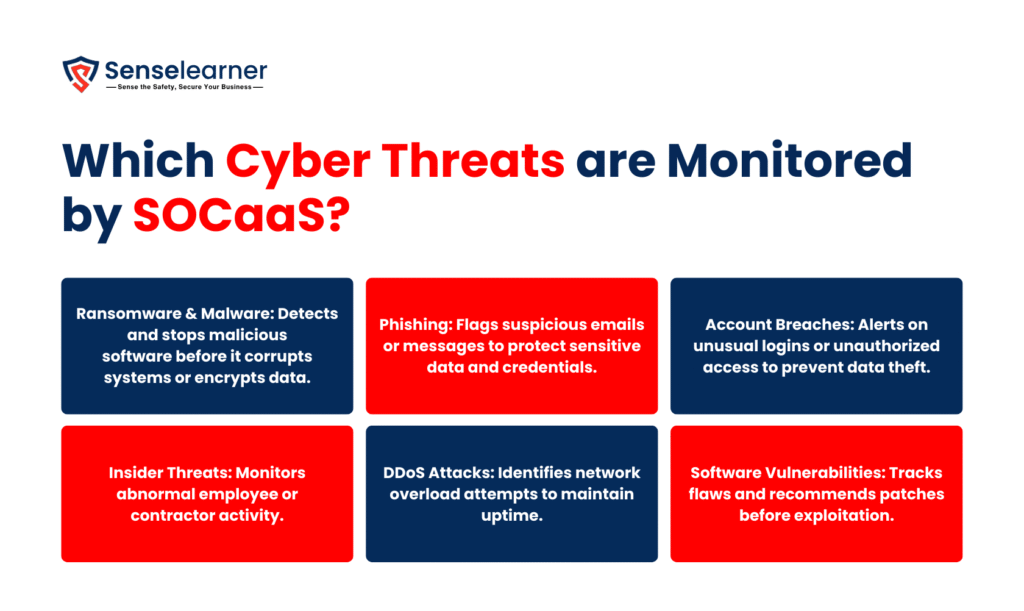
SOCaaS helps businesses stay safe by continuously identifying and addressing a variety of cyberthreats. SOCaaS helps enterprises to respond swiftly, minimize possible harm, and sustain seamless, safe operations by continuously monitoring these risks. Important threats consist of:
Malware and Ransomware Attacks: SOCaaS keeps a watch out for ransomware and malware attacks, which can corrupt computers or encrypt data until a ransom is paid. Data loss and operational impact can be avoided with early detection.
Phishing Attempts Targeting Employees: Suspicious emails or messages frequently try to obtain sensitive data or login credentials. These attacks are detected by SOCaaS before they compromise accounts.
Account breaches and unauthorized access: Unusual login attempts or attempts to access data that is restricted are reported. Security teams are alerted by SOCaaS to stop data theft and misuse.
Insider Threats and Suspicious Internal Activities: Workers or contractors may purposefully or unintentionally compromise security. To identify these threats early, SOCaaS keeps a watch out for abnormal behavior.
Distributed Denial-of-Service DDoS Attacks: SOCaaS detects attempts to overload networks or servers, preventing service interruptions and guaranteeing business continuity.
Software Vulnerabilities and Exploits: SOCaaS monitors software and application flaws and notifies enterprises to patch or address them before hackers can take advantage of them.
Key Components of SOCaas
For effective cybersecurity, SOCaaS depends on several essential components. All of these components work together to give the organization ongoing, proactive, and efficient cybersecurity through SOCaaS.
24/7 Monitoring: Continuous observation of network traffic, servers, endpoints, and apps guarantees that any unexpected activity is identified quickly, even outside regular business hours.
Incident Response Team: A dedicated group of security specialists analyzes alerts, investigates potential dangers, and responds rapidly to control and mitigate incidents.
SIEM, or security information and event management: It collects and examines security-related data from many sources in order to identify patterns, irregularities, and possible threats.
Threat intelligence: Enables proactive security measures by providing real-time updates on new cyberthreats, vulnerabilities, and attack methods.
Dashboards and Reporting: Management may make well-informed decisions by using visual and comprehensive reports that provide information on security incidents, system health, and overall risk.
Cloud and On-Premise Integration: Provides thorough coverage for all organizational infrastructure by monitoring and safeguarding resources on local systems as well as in the cloud.
Factors to Consider When Designing a SoC
Effective Security Operations Center (SOC) design requires careful planning and a comprehensive comprehension of organizational requirements. The capabilities of the SOC must be matched with company goals in order to guarantee that important assets and data are sufficiently safeguarded. To find potential risks and select technologies that work well with current systems, organizations must examine their risk landscape. It is important to carefully evaluate staffing and expertise to make sure that qualified individuals are available to oversee operations. Budgetary restrictions and the need to follow regulations must also be taken into account. Rapid threat detection, efficient incident response, and little operational disturbance are made possible by a well-designed SOC, which improves cybersecurity posture overall.
How SOCaas Works?
A mix of advanced technology, well-organized procedures, and knowledgeable cybersecurity analysts enables SOC-as-a-Service (SOCaaS) to operate. To provide complete network visibility, it starts with ongoing data collection from endpoints, servers, apps, and cloud environments. This data is processed by advanced programs, such as Security Information and Event Management (SIEM) systems and AI-driven analytics, to find unusual events, odd behavior, or possible threats. Automated alerts alert the security staff to unusual activities so they can look into them right away. After that, analysts evaluate the circumstances, eliminate dangers, and lessen harm. Proactive and efficient cybersecurity management is supported by comprehensive reports and dashboards that offer continuous insights into security posture.
SOCaaS Roles & Responsibilities
To maintain ongoing protection of an organization’s digital assets, SOC-as-a-Service includes a group of specialized roles, each of which is in charge of monitoring, identifying, and reacting to security risks.
Security analysts: Keep watch on security logs and alerts, look into odd activity, and report possible threats for additional action.
Incident Responders: Respond to security issues that are discovered, stop attacks as soon as possible, plan mitigation strategies, and make sure that business activities are not severely disrupted.
Threat Hunters: Use cutting-edge tools and threat information to actively look for hidden or developing dangers, spotting weaknesses before attackers take advantage of them.
SOC Manager: Leads SOCaaS operations, makes sure procedures are followed, leads the team, and updates management on security threats and status.
Compliance & Risk Specialists: To guarantee compliance, keep watch on legal requirements, implement security guidelines, and keep audit-ready records.
Together, these roles offer proactive threat management, quick reaction, and 24/7 monitoring, protecting the company from online attacks.
SOCaaS Implementation Best Practices
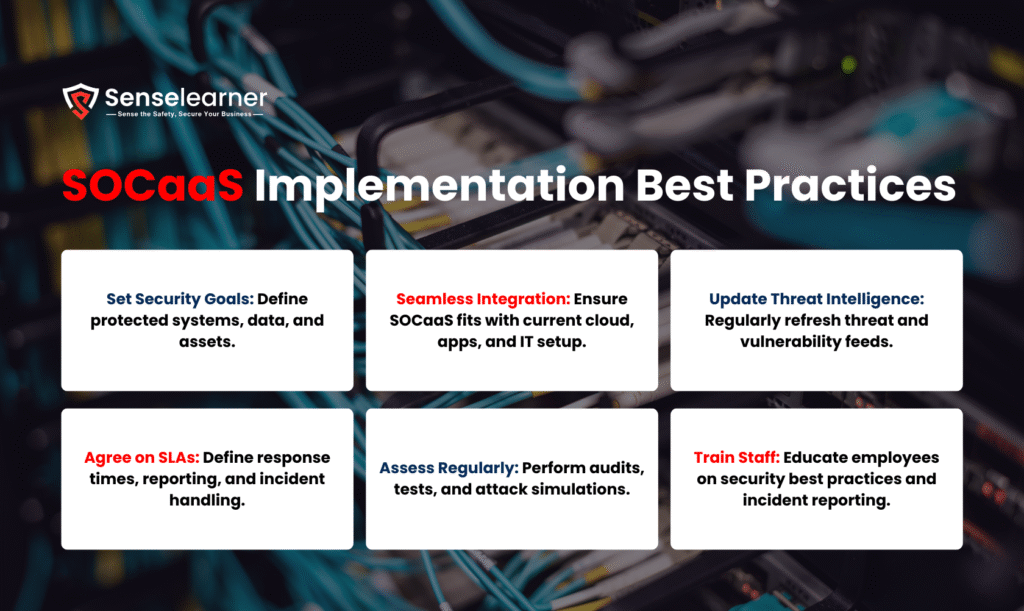
By following these guidelines, SOCaaS guarantees optimal protection, quick reaction, and compliance with enterprise security standards.
Define Clear Security Objectives: Establish clear objectives for SOCaaS installation and determine which systems, data, and assets require protection.
Integrate with Existing Systems:Ensure that SOCaaS tools and monitoring solutions integrate easily with the cloud, apps, and IT infrastructure that are in place now.
Keep Your Threat Intelligence updated:To keep ahead of new cyberthreats and vulnerabilities, update threat sources and information sources regularly.
Establish clear service level agreements (SLAs):Discuss response timeframes, reporting, and incident handling expectations with your SOCaaS provider.
Conduct Regular Assessments: Use security audits, testing, and simulated attack scenarios to periodically assess the efficacy of SOCaaS.
Train Employees in Security Procedures: To reduce insider threats and human error, train employees in safe procedures, incident reporting, and alert management.
Benefits of Soc – as- a- service
Without the need for an entire in-house workforce, SOC-as-a-Service (SOCaaS) gives businesses an economical and effective approach to maintain strong cybersecurity. It ensures that threats are identified in real time by offering 24/7 network, endpoint, and cloud system monitoring. Businesses have access to knowledgeable cybersecurity experts who evaluate events and suggest solutions. SOCaaS allows for quick incident response to reduce damage and is scalable, changing to meet expanding business needs. By offering reporting and audit-ready paperwork, it helps as well with regulatory compliance. All things considered, SOCaaS gives businesses peace of mind, improves security posture, and lowers operational complexity.
The Role of a SOC Team in Cybersecurity
24/7 Threat Monitoring: To identify unusual behavior or security issues in real time, SOC teams keep constant watch on networks, systems, endpoints, and applications.
Incident Detection & Response: In order to reduce damage and downtime, the team quickly investigates, contains, mitigates, and recovers from threats when a cyberattack takes place.
Vulnerability & Risk Management: To stop exploitation, SOC teams find flaws in the system, apply fixes, and enhance security.
Threat Intelligence & Analysis: SOC teams can proactively modify protection measures and predict new attack methods by utilizing global threat intelligence feeds.
These positions guarantee that businesses maintain operational continuity while being safeguarded against changing cyberthreats.
SOC Solutions for Your Company
SOCaaS suppliers like Senselearner add useful services to their solutions, which may be modified to fit various business needs. For companies that depend significantly on cloud apps, cloud-only SOCaaS is perfect. Senselearner protects cloud infrastructure on AWS, Azure, and GCP platforms, and SOCaaS keeps an eye out for threats to guarantee secure and continuous operations. Cloud and on-premises system monitoring are combined in hybrid SOCaaS, and Senselearner assists in integrating security across all environments for comprehensive protection. In addition to Senselearner’s VAPT and vulnerability management, Managed Detection and Response (MDR) provides proactive threat hunting and incident response.
Sector-specific SOCaaS targets industries like e-commerce, healthcare, and finance, matching services to industry-specific risks and regulatory requirements. With the help of Senselearner’s risk management and audit-ready reporting, compliance-focused SOCaaS guarantees adherence to GDPR, HIPAA, PCI DSS, and ISO standards. Businesses of all sizes can benefit from a reliable, scalable security framework that combines SOCaaS with Senselearner’s services to provide comprehensive monitoring, proactive threat detection, regulatory compliance, and dependable cybersecurity.
FAQ’s
What differentiates SOCaaS from traditional SOC?
Building and maintaining an internal security team, tools, and infrastructure is necessary for a standard SOC, and this can be costly and resource-intensive. In contrast, SOC-as-a-Service (SOCaaS) is provided via the cloud and is managed by outside professionals. It is more scalable, economical, and available to companies of all sizes since it offers 24/7 monitoring, threat identification, and incident response without the overhead.
Is it possible to integrate SOCaaS with current security tools?
Yes, SOCaaS is made to enhance current security and IT architecture. It offers continuous monitoring and threat detection by integrating with on-premises systems, cloud services, and apps. Integration with products like firewalls, SIEM systems, and endpoint protection is also supported by a lot of suppliers. This guarantees that companies may improve their present systems with advanced monitoring and expert-driven issue response, rather than having to replace them.
Is SOCaaS appropriate for small companies?
Yes, small firms face the same cyber hazards as larger corporations, but they sometimes lack the resources and know-how to maintain a comprehensive in-house SOC. Without hiring a specialized security team, SOCaaS provides them with reasonably priced, 24/7 security monitoring and professional assistance. Due to its scalability, small firms can begin with basic services and grow as needed, guaranteeing cost-effective security against changing threats.
Conclusion
Businesses looking to improve cybersecurity without facing the high expenses of establishing an internal SOC now find that SOC-as-a-Service, or SOCaaS, is a key solution. SOCaaS helps businesses stay ahead of changing threats by providing scalable security, expert-driven incident response, and 24/7 monitoring. Companies of various sizes and in a variety of sectors can use it due to its adaptability, which ensures both operational continuity and compliance. SOCaaS adoption is a calculated step toward establishing long-term resilience in the digital era, in addition to being a cost-effective option.



